37
10 Tips for Safe and Secure Remote Work for Developers
Modern employees require more flexibility than their previous counterparts.
But shifting from in-person work to remote work comes with a full host of changes (and something to keep in mind when starting a business). The most crucial one? Making sure your remote team is set up to work safely and securely.
But before we touch on 10 tips to improve your remote team’s security, let’s take a look at the importance of safe and secure remote working.
Now that more employees are working remotely, many companies are using cloud based workflows, cloud communication platforms or other cloud management solutions, and office management software, so everyone has access to real-time information and documents. That way, the process of tracking developer productivity get also simplified. With employees being able to access company information from anywhere in the world, data security is more important than ever.
But the average remote employee may not have the set-up that businesses require to protect sensitive and proprietary information.
Without business-grade security, businesses are leaving themselves open to compliance issues, brand damage, leaked data, financial loss, and other legal and costly risks.
That’s why it’s crucial to be proactive about protecting your business’s security.
To protect your business, check out the following 10 safety tips.
Our first tip for increasing home and remote network security is providing employees with access to a virtual private network (VPN).
VPNs act like a highly protected tunnel within another network connection you manage. All data stays within the tunnel, meaning:
VPNs also unlock geographically restricted internet pages without encrypting your traffic (so it doesn’t affect your internet speed). Finally, you'll have a chance to check your favorite sites or other quality content materials worldwide.
When choosing a VPN, look for one that offers 24/7 customer support, native apps for multiple operating systems and devices, and international servers, like ExpressVPN does.
Because of this, HR teams need a way to access important data to do their jobs without sacrificing security. The answer?
Storing data securely and making it accessible to the right people.
To do this, you’ll either need to use a tool like Microsoft’s Compliance Manager in Microsoft 365 or you can hire a professional employer organization (PEO) service provider to handle it for you.
Remote working means that you’ll likely hire your team (developers, product managers, web designers etc.) without seeing them face-to-face.
From non-disclosure agreements to work contracts and W-4s, new employees have a lot of forms to sign.
To make sure your onboarding process is secure, you’ll need to use contract management software.
This ensures that all documents are:
Having a safe contract signing process is also important for other contracts and forms, such as:
Collaboration and file sharing are integral parts of a remote business.
Whether it’s NDA, copy templates, product description, or ad copy – all documents have to be shared securely across the whole team.
Using premium collaboration tools is a more secure way to share files because of the tools' advanced built-in security features.
To help your employees securely share files, consider using protected PDFs and private Google docs with assigned permissions.

Make sure to encourage your employees to refrain from collaborating and sharing files through email. Although sharing through email is usually quick and easy, it’s best to avoid communicating and transferring files this way if confidential information is involved.
If you have to use email to send or receive a file, always triple-check where it’s coming from or where you’re sending it to make sure it’s a valid and secure email address.
Also, if you want to bring your advertising metrics into Google Workspace, you can increase productivity by using a Google spreadsheet add-on. Make sure it is a Premier Google Partner, since this guarantees you that this process is 100% secure.
When employees use their own devices to work from home, they tend to use devices that are less secure than business-issued devices.
It’s possible that:
Even worse, they could be accessing insecure websites like torrents or suspicious sites using those same devices. This increases the risk of data leaks and viruses plaguing your confidential files.
To avoid this, consider issuing professional devices to your employees that your IT team recommends. If this isn’t possible, see if your IT team can tighten the security around your employees’ personal devices.
Your business probably already uses cybersecurity tools to protect against phishing, viruses, malware, and ransomware on business hardware.
But if employees are using personal devices for work, they need high-level protection too.
To make sure they use antivirus software, provide them with security software programs and ask them to show you proof that they’ve been installed. You can also provide a list of acceptable security software programs as an alternative.
In the end, there’s no way around it — everyone needs antivirus software to work safely.
Implementing remote work security policies shows your team that your business is serious about having security measures in place. This also holds your staff accountable for working securely.
After choosing which policies to implement, be a virtual mentor and make sure to coach your team, so they fully understand what’s expected of them.
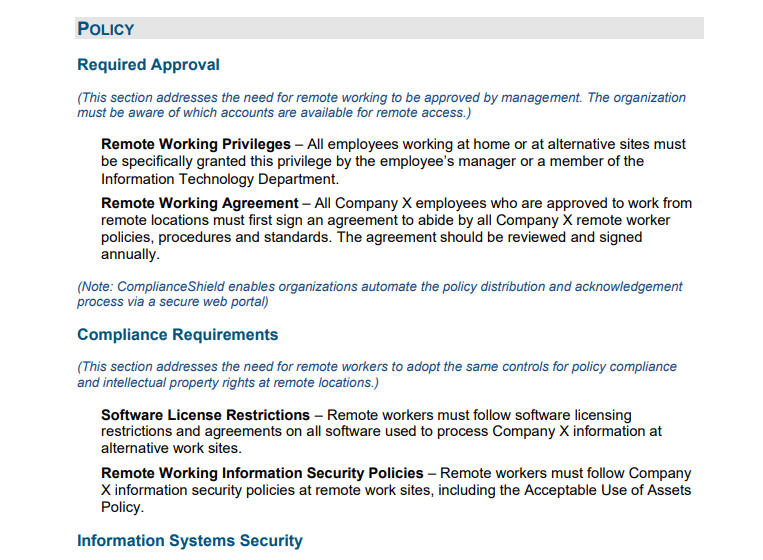
Your security policies may include rules about:
Whether it's a software project or remote policy – make sure to have a proper implementation plan.
Employees often feel nervous reporting suspicious attempts or potential cyber incidents. They may fear losing their job, getting penalized, or being questioned about breaching security policies.
But encouraging employees to report cyber incidents can make them feel more comfortable about coming forward when something happens.
To foster open communication, create a single source dedicated to reporting suspicious activity via a dedicated messaging group, Slack channel, or IT support email. This way, they’ll know exactly how to report the incident when they’re working from home or coworking space.
It’s also important to ask employees to report suspicious activity, even if they broke one of your security policies. To encourage them to do this, ensure employees that they won’t face harsh disciplinary action if they come forward. Then, offer additional security training so they can be better equipped to follow policies in the future.
Conducting security training in the form of webinars, workshops, and video classes helps employees better understand how to work safely. For this, there are tons of useful online video editors, webinar platforms or course platforms

When deciding on a training program, choose one that’s hands-on. This way, employees can practice sharing files, updating software, configuring their routers, installing virus protection, and using VPNs.
One more important point, use LastPass as a password management system or any other LastPass alternative.
It’s also important to explain exactly what to do if something goes awry.
Remember, security is a team effort. It’s not really a question of if you’ll have a security breach, but rather when you’ll have one.
To make sure your business will still be up and running when that happens, have backup systems in place.
What will you do if an employee’s device is stolen?
What will you do if a manager accidentally opens a phishing email?
Have a backup plan in place in case anything happens. That way, you won’t lose productivity, even if your systems and networks are breached.
And that’s it! We hope these 10 tips for safe and secure remote working are just what you needed to read.
With careful planning and training, your team will be on its way to operating as securely as possible.
Are you curious about the history of cloud-based workflows, AKA the main reason businesses can operate and collaborate remotely? Then check out our podcast episode “The History of the Cloud.”
37
