37
2 Widespread Attacks on Your Containerized Environment and 7 Rules to Prevent it.
The MITM attack is widespread in the Kubernetes and Docker. This attack includes additional malicious parts between the component that sends data and the component that receives this data. It can be a fake container, service, middleware, or even a human. For example:
This attack allows an attacker to run the malicious code to use the CPU, GPU, and Memory of the PC for mining cryptocurrencies. Example:
The container itself is a small OS that can be susceptible to attack with malicious code. In this article, we talk about
I consider using Docker and Kubernetes as two current leaders in container engines and orchestration.
This principle means that you should not execute containers using admin users. You should create users that have admin access and can only operate with this particular container. You can also make groups add users there. You can read more about it in “Isolate containers with a user namespace”. Below is an example of how to create the user and group.
First of all, you should use official verified and signed images. To find and check images you can use docker trust inspect.
For example docker trust inspect — pretty google/apigee-mart-server:1.3.6.
Docker Content Trust (DCT) can help with digital signatures.
It allows verification of images and publishers during runtime. This process is based on (Docker Content Trust Keys)[https://docs.docker.com/engine/security/trust/#docker-content-trust-keys], which generates several keys during the first interaction with DCT.
You should set up Memory and CPU limits for your docker container because docker has a container that does not have this option by default. This principle is a way to prevent DoS attacks. For example, you can set up a Memory limit to prevent your container from consuming all memory. The same applies to CPU limits.
There is also an option to set up resource limits on a Kubernetes level. I cover this topic in the Kubernetes Security section.
This principle is essential to understand Docker’s networking principles. You should understand what Docker Network Drivers are, for example:
By default, one container network stack does not have access to another container. However, if you configure bridged or host to accept traffic from any other containers or external networks, you can create a potential security backdoor for an attack. You can also disable inter container communication using just set flag
— icc=false within docker daemon.Security monitoring is essential for the detection of malicious code and attacks on your containers.
With a proper monitoring tool, you should be able to detect the issues.
The tool allows you:
To find the vulnerability in Docker containers, you can use
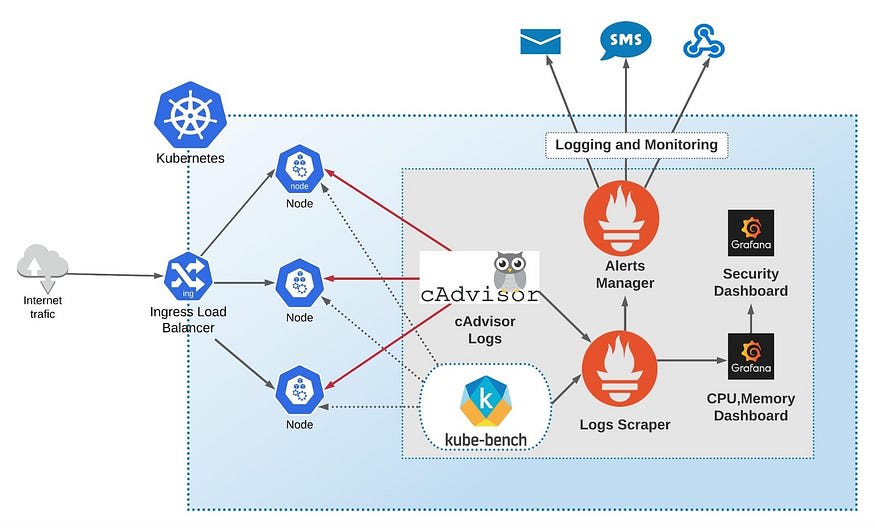
docker scan command.Docker scan or Caadvisor is a simple solution that applies to only one particular container. For more complex scenarios, for example, when you run 50+ containers in the Kubernetes, you need complex monitoring tools such as:
Also, I use the security tool Kube-bench that covers vulnerabilities scanning only. The Kubebench brings an additional layer to your cluster security monitoring. There are plenty of security tools available for Kubernetes.
This principle is quite important to move all sensitive data out of the container. You can use different options to manage your secrets and other sensitive data:
Vulnerability scanning tools are the essential part of detecting images that may have security holes. Moreover, you can also integrate properly selected tools into the CI/CD process. Below I have listed some scanning tools:
You can find more in the Containers Trend Report article.
To protect your images, you can create an additional security layer and use images from protected registries like:
But what if you are already using other registries like Azure Container Registry or Docker Hub? You can find how to do it in the Containers Tend Report article.
Kubernetes security is a big and important topic. The main security rules are:
The security principles that are mentioned in the docker container section
To find security and misconfiguration in kubernetes, you can use the following tools:
Security Topic is very important and complex, especially in the Docker and Kubernetes world. This article contains the most important recommendations to be taken into account. You can find more information about Containers Trends in the Containers Tend Report.
37
