18
Understanding HTTPS
In this post, we are going to deep dive into HTTPS.
This post contains the following points:
It is a protocol from the application layer used for the transfer of hypertext, image, videos, etc from client to server.
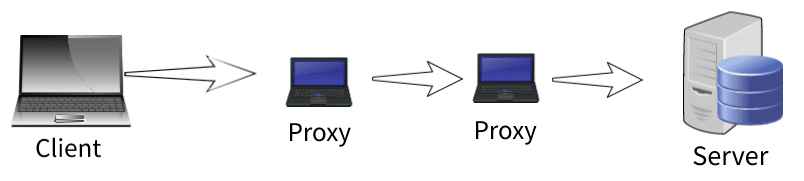
During client-server communication, the data travels from several devices which are called proxies.
During client-server communication, the data travels from several devices which are called proxies.
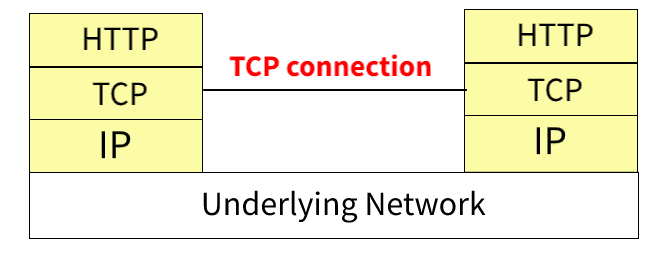
Before a client and server can exchange an HTTP request/response pair, they must establish a TCP connection, a process that requires several round-trips.
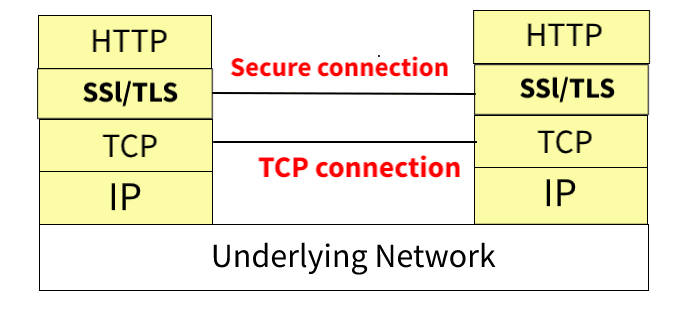
After successful connection client can send requests to & read responses from the server. Then it can reuse the connection or can close it.
HTTPS is just a secure HTTP connection between client & server needed to achieve 3 main goals:
To make the connection secure SSL/TLS security gets added to the previous HTTP stack.
To transfer data between any two entities securely on the internet it should be encrypted using some encryption technique. Cryptographic algorithms are used to make such encryption.
Let's talk about the two types of encryption algorithms.
Let's talk about the two types of encryption algorithms.
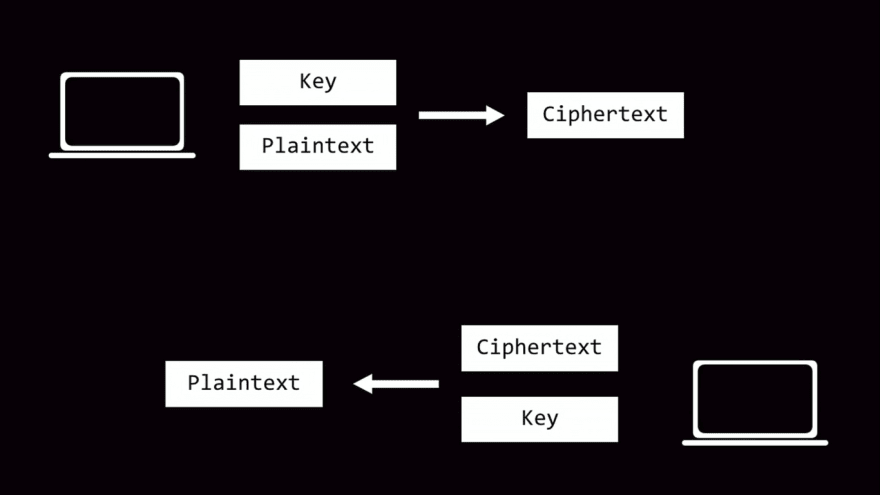
 public key has the ability to only encrypt the message & only the private key can decrypt it.
public key has the ability to only encrypt the message & only the private key can decrypt it.
Secret key cryptography can't be used directly for communication on the internet. But Public-Private key cryptography is computationally costly than its counterparts in secret-key cryptography.
Also there is one more caveat, anyone in between client and server such as proxy servers as shown above can pretend that they are the actual server.
For ex: If you made a request to google.com from a browser and the device in between can pretend that they are actually google and send you a response and maintaining connection from their own end to google server. This is called a middle man attack.
For ex: If you made a request to google.com from a browser and the device in between can pretend that they are actually google and send you a response and maintaining connection from their own end to google server. This is called a middle man attack.
To prevent that there are third-party Certification Authorities present. A root store is basically a database of trusted CAs which is preinstalled on each browser.
Let's take a walkthrough of how HTTPS achieved:
Then server reaches to CA and gives it's public key to get CA signed Public key certificate.
Sends this certificate to the client in response. The client verifies that this response is from a valid source by decrypting the signature present in the signed certificate.
If valid then it generates the pre-master key and sends it to the server encrypting with the public key sent in a previous response.
On server, it decrypts data using the private key present.
Now they both generate the same 'shared secret' that they are going to use as a symmetric key to encrypt and decrypt data.
This is called a TLS handshake.
Well, this is how both secret-key & public-private key cryptography are used in combination to achieve HTTPS connection.
18

