33
Architecting Amazon EKS for PCI DSS Compliance Summary | AWS Whitepaper Summary

• Provides technical and operational guidance on securing payment card processing environments
• Entities that store, process, or transmit cardholder data (CHD) must be PCI DSS certified ,so they have proven that the followed policies ,procedures, guidelines and best practices to build cardholder data environment (CDE)
• Entities that store, process, or transmit cardholder data (CHD) must be PCI DSS certified ,so they have proven that the followed policies ,procedures, guidelines and best practices to build cardholder data environment (CDE)
• AWS provided many services that meet PCI DSS Compliance
• AWS Artifact: a central resource for compliance-related information. It can be accessed by companies, on-demand, to reduce compliance efforts .The services provided are containerized by AWS. So companies take advantage of platform independence, deployment speed and resource efficiency.
PS: A service listed as PCI DSS compliant doesn’t mean that it makes a customer’s compliant by default.
• AWS Artifact: a central resource for compliance-related information. It can be accessed by companies, on-demand, to reduce compliance efforts .The services provided are containerized by AWS. So companies take advantage of platform independence, deployment speed and resource efficiency.
PS: A service listed as PCI DSS compliant doesn’t mean that it makes a customer’s compliant by default.

PCI DSS compliance status of AWS Services
• AWS is a Level 1 PCI DSS Service Provider: AWS customers meet easily compliance requirements.
• AWS is a Level 1 PCI DSS Service Provider: AWS customers meet easily compliance requirements.
• Any data provided by the customer has :
•The annually updated PCI DSS assessment includes physical security requirements for AWS datacenters.
AWS Shared Responsibility model
Security and compliance responsibilities and shared between AWS and the customer.
AWS Shared Responsibility model
Security and compliance responsibilities and shared between AWS and the customer.
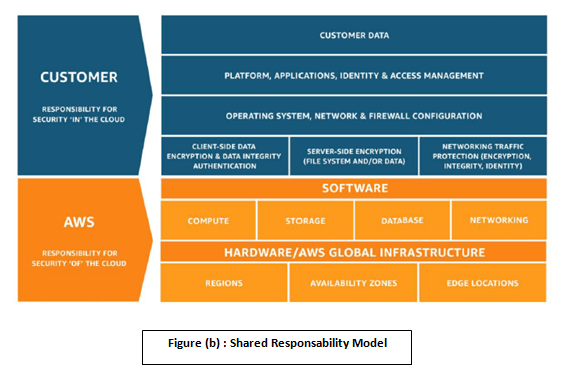
• AWS : Security , management, control of AWS cloud infrastructure (Hardware ,software, networking and facilities)
• Customer: Security of all the systems components and services provisioned on AWS (included in or connected to the customer’s CDE) like access control ,log settings, encryption , etc
PCI DSS scope determination and validation
The cardholder data flow determines:
• Applicability of PCI DSS
• Scope of PCI DSS; boundaries and components of CDE
-The customer must have a procedure for PCI DSS scope determination to assure its completeness and to detect changes and violations of the scope.
-Steps that comprise the PCI DSS scope identification are:
The cardholder data flow determines:
• Applicability of PCI DSS
• Scope of PCI DSS; boundaries and components of CDE
-The customer must have a procedure for PCI DSS scope determination to assure its completeness and to detect changes and violations of the scope.
-Steps that comprise the PCI DSS scope identification are:

PS: Customers need to be aware of container configuration parameters through all the phases of a container lifecycle to ensure the satisfaction of the compliance requirements.
While architecting a container-based environment for PCI DSS compliance, you have to follow the best practices recommendations for those key topics:
• Network segmentation
• Host and container image hardening
• Data protection
• Restricting user access
• Event logging
• Vulnerability scanning and penetration testing
• Network segmentation
• Host and container image hardening
• Data protection
• Restricting user access
• Event logging
• Vulnerability scanning and penetration testing
To enforce your VPC’s network policy you can use Calico is an open-source policy engine from Tigera.It works well with Amazon EKS supports extended network policies and can be integrated with service mesh .
• Security groups act as a virtual firewall and provide stateful inspection, they restrict communications by IP address, port, and protocol.They are used by Amazon EKS to control the traffic between the Kubernetes control plane and the cluster's worker nodes.
PS: It is strongly recommended that you use a dedicated security group for each control plane (one for each cluster).
• Individual AWS accounts for PCI DSS provide the highest level of segmentation boundaries on the AWS platform. Their resources are logically isolated from other accounts.
• Security groups act as a virtual firewall and provide stateful inspection, they restrict communications by IP address, port, and protocol.They are used by Amazon EKS to control the traffic between the Kubernetes control plane and the cluster's worker nodes.
PS: It is strongly recommended that you use a dedicated security group for each control plane (one for each cluster).
• Individual AWS accounts for PCI DSS provide the highest level of segmentation boundaries on the AWS platform. Their resources are logically isolated from other accounts.
• To isolate containerized application communications ,you need to :
1) Isolate pods on separate nodes based on the sensitivity of services and isolate CDE workloads in a separate cluster with a dedicated Security group.
2) Use AWS security groups to limit communication between nodes and control plane and external communications.
3) Implement micro-segmentation with Kubernetes network policies and consider the usage of the service mesh, Networking and Cryptography library (NaCI) encryption and Container Network Interfaces (CNIs) to limit and secure communications.
4) Implement a network segmentation and tenant isolation network policy.
Host and image hardening (Requirement N°2)
Host and image hardening help to minimize attack vectors by disabling support for vendors for security parameters.In which:
• Customers should create trusted base container images that have been assessed and confirmed to use patched libraries and applications. Use a trusted registry to secure container images, such as Amazon Elastic Container Registry (Amazon ECR). Amazon ECR provides image scanning based upon the Common Vulnerabilities and Exposures (CVEs) database and can identify common software vulnerabilities.
• Container optimized Amazon Machine Image (AMI) contains only essential libraries for deployments. Non-essential services and libraries should be disabled or removed.
• Container builds should be limited and should adopt a model of microservices where a container provides one primary function.
• It is recommended to use special-purpose operating systems (OS) like Bottlerocket that includes a reduced attack surface , a disk image that is verified on boot, and enforced permission boundaries using SELinux.
• Establish configuration standards under the shadow of the industry-accepted system hardening guidelines.
Data protection (Requirements N°3 and 4)
This is about the PCI DSS requirement to protect sensitive data in rest and in transit. PCI DSS compliant services and features to assist with these compliance efforts.
Host and image hardening help to minimize attack vectors by disabling support for vendors for security parameters.In which:
• Customers should create trusted base container images that have been assessed and confirmed to use patched libraries and applications. Use a trusted registry to secure container images, such as Amazon Elastic Container Registry (Amazon ECR). Amazon ECR provides image scanning based upon the Common Vulnerabilities and Exposures (CVEs) database and can identify common software vulnerabilities.
• Container optimized Amazon Machine Image (AMI) contains only essential libraries for deployments. Non-essential services and libraries should be disabled or removed.
• Container builds should be limited and should adopt a model of microservices where a container provides one primary function.
• It is recommended to use special-purpose operating systems (OS) like Bottlerocket that includes a reduced attack surface , a disk image that is verified on boot, and enforced permission boundaries using SELinux.
• Establish configuration standards under the shadow of the industry-accepted system hardening guidelines.
Data protection (Requirements N°3 and 4)
This is about the PCI DSS requirement to protect sensitive data in rest and in transit. PCI DSS compliant services and features to assist with these compliance efforts.
Protect the data in rest:
Secure all the sensitive stored data of PCI DSS workloads on secure stores or databases NOT on the container host.
• Consider the use of AWS Key Management Service (KMS) to secure encryption key storage, access controls and annual rotation.
• Use AWS Secrets Manager and AWS Systems Manager Parameter Store to secure sensitive data within container build files.
• Consider the use of AWS Key Management Service (KMS) to secure encryption key storage, access controls and annual rotation.
• Use AWS Secrets Manager and AWS Systems Manager Parameter Store to secure sensitive data within container build files.
Protect the data in transit:
PCI DSS urges the encryption of sensitive data during transmission over open, public networks. Customers are responsible for configuring strong cryptography and security controls.
• Consider a variety of AWS services like Amazon API Gateway and Application Load Balancer
• Encryption in transit for inter-pod communication can also be implemented with a service mesh like AWS App Mesh with support for mTLS.
• Use envelope encryption of Kubernetes secrets in EKS to add a customer-managed layer of encryption for application secrets or user data that is stored within a Kubernetes cluster.
• Consider a variety of AWS services like Amazon API Gateway and Application Load Balancer
• Encryption in transit for inter-pod communication can also be implemented with a service mesh like AWS App Mesh with support for mTLS.
• Use envelope encryption of Kubernetes secrets in EKS to add a customer-managed layer of encryption for application secrets or user data that is stored within a Kubernetes cluster.
Other protection measures:
• Restrict access to authorized personnel(Requirement N°7 and 8), grant least privileges and authenticate with strong authentication requirements that align with the PCI DSS.
• Run containers with non-privileged user accounts and restrict all access to container images.
• Consider disabling the use of the secure shell (SSH) and instead leverage AWS Systems Manager’s Run Command
• Urge that users sign into the Amazon EKS cluster with an IAM identity(either an IAM user or IAM role)
• Create the cluster with a dedicated IAM role which should be regularly audited.
• Make the Amazon EKS Cluster endpoint private.
• Run containers with non-privileged user accounts and restrict all access to container images.
• Consider disabling the use of the secure shell (SSH) and instead leverage AWS Systems Manager’s Run Command
• Urge that users sign into the Amazon EKS cluster with an IAM identity(either an IAM user or IAM role)
• Create the cluster with a dedicated IAM role which should be regularly audited.
• Make the Amazon EKS Cluster endpoint private.
Tracking and monitoring access (Requirement N°10)
This is about the use of event logs to track suspicious activities and even anticipate possible threats. So:
• EKS Cluster audit logs need to be enabled as well as VPC Flow Logs, Amazon CloudWatch and Amazon Kinesis
• CloudWatch dashboard should be configured to monitor and alert on all captured event log activity
• Captured event data have to be stored securely within encrypted Amazon S3 buckets to be analyzed with Amazon Athena and Amazon CloudWatch Logs Insights.
• Amazon GuardDuty provides threat detection .
Network Intrusion detection(Requirement N°11)
• Monitoring of all traffic at the perimeter and critical points of the CDE
• Use network inspection options outside of the container host on AWS like :
Amazon GuardDuty: a managed service that provides threat detection across multiple AWS data sources to identify threats.
Amazon VPC Traffic Mirroring: traditional IDS/IPS solution.
Virtual IDS/IPS device from the AWS Marketplace: helps to inspect in transit traffic.You can use a VPC Gateway to route all traffic to on-premises IDS/IPS infrastructure.
Vulnerability scanning and penetration testing(Requirement N°11.2)
It aims to test systems and processes regularly to identify and fix vulnerabilities.
• Penetration testing is to be performed on an annual basis and after any significant environmental changes.
• Penetration testing of AWS resources is allowed at any time for certain permitted services in the perimeter of the penetration testing policy .
• PCI DSS Compliance provides guidance and methodologies to perform penetration testing .It depends on customer’s environment.
• When deploying Amazon EKS on Amazon EC2 instances, customers must perform vulnerability scanning of the underlying host.
• Amazon Inspector is a security assessment tool that helps identify vulnerabilities and prioritizes findings by level of severity.
• The Center for Internet Security (CIS) Kubernetes Benchmark provides guidance for Amazon EKS node security configurations.
This is about the use of event logs to track suspicious activities and even anticipate possible threats. So:
• EKS Cluster audit logs need to be enabled as well as VPC Flow Logs, Amazon CloudWatch and Amazon Kinesis
• CloudWatch dashboard should be configured to monitor and alert on all captured event log activity
• Captured event data have to be stored securely within encrypted Amazon S3 buckets to be analyzed with Amazon Athena and Amazon CloudWatch Logs Insights.
• Amazon GuardDuty provides threat detection .
Network Intrusion detection(Requirement N°11)
• Monitoring of all traffic at the perimeter and critical points of the CDE
• Use network inspection options outside of the container host on AWS like :
Amazon GuardDuty: a managed service that provides threat detection across multiple AWS data sources to identify threats.
Amazon VPC Traffic Mirroring: traditional IDS/IPS solution.
Virtual IDS/IPS device from the AWS Marketplace: helps to inspect in transit traffic.You can use a VPC Gateway to route all traffic to on-premises IDS/IPS infrastructure.
Vulnerability scanning and penetration testing(Requirement N°11.2)
It aims to test systems and processes regularly to identify and fix vulnerabilities.
• Penetration testing is to be performed on an annual basis and after any significant environmental changes.
• Penetration testing of AWS resources is allowed at any time for certain permitted services in the perimeter of the penetration testing policy .
• PCI DSS Compliance provides guidance and methodologies to perform penetration testing .It depends on customer’s environment.
• When deploying Amazon EKS on Amazon EC2 instances, customers must perform vulnerability scanning of the underlying host.
• Amazon Inspector is a security assessment tool that helps identify vulnerabilities and prioritizes findings by level of severity.
• The Center for Internet Security (CIS) Kubernetes Benchmark provides guidance for Amazon EKS node security configurations.
AWS provides a convenient infrastructure for customers to address PCI DSS requirements for their containerized workloads. Various security measures are ready to use in order to reduce management complexities for the users.
33


