23
Landing Zones, Organizations, OUs and Multi-Account Environments
Governance, risk, and compliance when establishing your cloud presence (AWS Blog Page)
Organizational Units with AWS Organizations (AWS Blog Page)
Managing the multi-account environment using AWS Organizations and AWS Control Tower (AWS Blog Page)
A Landing Zone is a...Well-architected multi-account AWS environment that is stable and secure
It is:
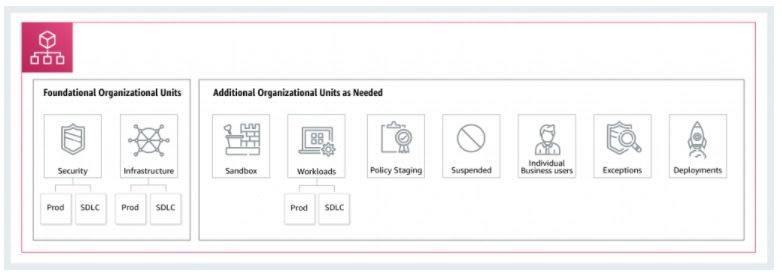
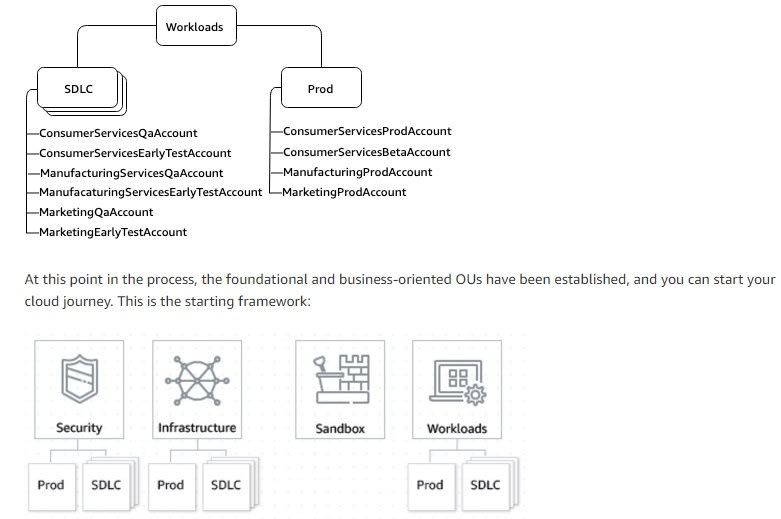
Shared Services OU is for things like log archival, networking - Usually the responsibility of central teams
2 Tools to assist here...
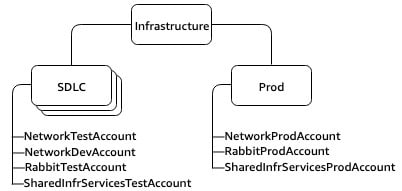
SDLC OUs - Think of having SCPs at each stage of the lifecycle of the application

e.g Different Policies in different Stages/Environments (Dev vs Test)
Deployments OU - If you have different governance and operational models for CICD compared to accounts in Workloads OU (Prod / SDLC)
** Reduces dependency on shared CI/CD environments
** Pipelines and CICD should match the operational model of the software service it builds and deploys

Security OU for hosting security-related services, should be managed by Security team(s)

Log Archive - Audits
ReadOnlyAccess - Humans for Read-Only permission, cross-account role from here
Breakglass - Humans in rare scenarios/security incidents, special authorisation would be required, all access to this logged in detail
Tooling - MINIMAL Humans, Master Account for Guard Duty, Security Hub and Amazon Detective...Human Access for Admin purposes only, infrequent
** IaC should be heavily used
Sandbox OU for individuals wanting to play, should limit internet access if possible
** Individuals Accounts created in here e.g ColinWillisAccount
Suspended OU - Accounts that are to be deleted from the Organisation
** Apply an SCP to deny all actions, add Tags for traceability if they need to be restored
** Accounts are permanent deleted after 90 days
Exceptions OU - Accounts that warrant exceptions to Security or Auditing conditions
** SCP may be applied directly to the accounts here
Think Top-Secret Project Account; it may have MORE scrutiny than standard accounts
** Preventative guardrails are SCPs that limit actions based on your policies.
** Detection guardrails are AWS Config rules paired with AWS Lambda
*** These detect noncompliant resources and alert you through the Control Tower dashboard for remediation
AWS Audit Manager - automates the continuous collection of evidence to help you audit your use of cloud services.
AWS Config - detects and provides mitigation recommendations for incorrectly configured resources.
Amazon GuardDuty - detects unexpected and potentially unauthorized and malicious activity in your AWS environment.
Amazon Macie - continuously evaluates your content to identify business-critical or potentially confidential data.
AWS Trusted Advisor - identifies opportunities to improve stability, save money, or help close security gaps.
IAM Access Analyzer - helps you identify any resources or data in your AWS environment that are shared with external entities.
AWS Security Hub - provides you with security checks and recommendations across your organization.** AWS Resource Access Manager - Make resources available cross-account e.g EC2 Capacity Reservation, VPC Endpoints
** AWS CloudFormation StackSets - Share Stacks cross account e.g Automatically delete or create resources when an Account joins or leaves the Organization
23