20
AWS VPC Basics. Building your first VPC with a public and private subnet
Hey there!
Manually building your first VPC with a public and private subnet should definitely be one of your AWS newbie tasks, it will allow you to quickly get a grasp of how VPCs work and what we are trying to do here and why.
Of course you can use the VPC wizard to do this but it is helpful just to create your first VPC manually, this way you can get an indication of the subnet ranges and services required to get you going with your very first VPC that has both a public and private subnet, both ready to host ec2 instances.
These are the things we want to accomplish here:
- Select an AWS region
- Create a VPC (a virtual private data centre) within the selected region.
- Assign a /16 network address range to our VPC
- Consider the subnets ranges you want to use with the VPC address range (we will be using /24)
- Create a single public subnet for one availability zone
- Attach an Internet Gateway for our public subnet.
- Create a single private subnet for one availability zone.
We are using single availability zones only (designing fault tolerant distributed systems across multiple availability zones would be something that you would definately do in production)
Let's get started.
Login to the AWS console and then choose the region at the top right (I am going for London, eu-west-2)

Now hit the services drop down option at the top and choose VPC (under Networking & Content Delivery) - from there hit create VPC at the top right.

Next up, use the following details to fill in the VPC form:
- Name tag [your-vpc-name]
- IPv4 CIDR block [10.0.0.0/16] - this will give us 65,536 IP addresses to split up across the whole VPC in various subnet ranges.
- Tenancy, choose Default
- I have put some resource tags in as examples
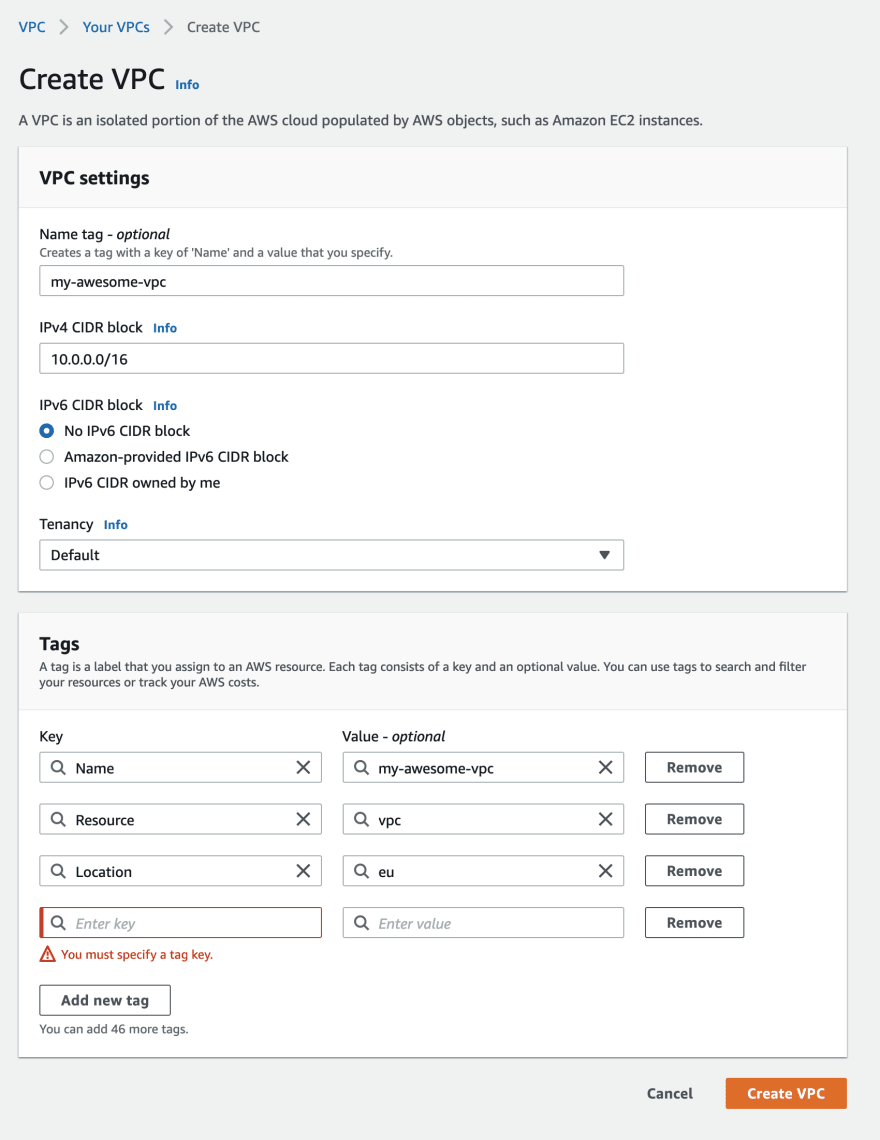
Hit create.
You should still be in the VPC part of the AWS console, so look to the left and there will be a link to subnets, hit that link.

At the top right, hit create new subnet
- Select the VPC that we just created
- Let's give the subnet a relevant name. I am going for 'public-subnet-myawesomevpc-eu-west-2a' (specifying public or private, resource type, vpc name and then region/az)
- For this example I am going for a /24 subnet in each AZ giving us a total of 254 per subnet (excluding management IPs) so 10.0.0.0/24
- Hit create

Okay so what makes the public subnet actually 'public' and different than the private subnet? The answer is simple, you attach an Internet Gateway to your VPC and then update the associated routing table to allow Internet traffic in and out of the subnet.
Let's do that now:
Still in the VPC dashboard, under subnets, hit 'Internet gateways'
Top right again, hit create new Internet Gateway. From there, fill in the Internet gateway form:
- Name, fill in a descriptive name
- Tag the resource appropriately.
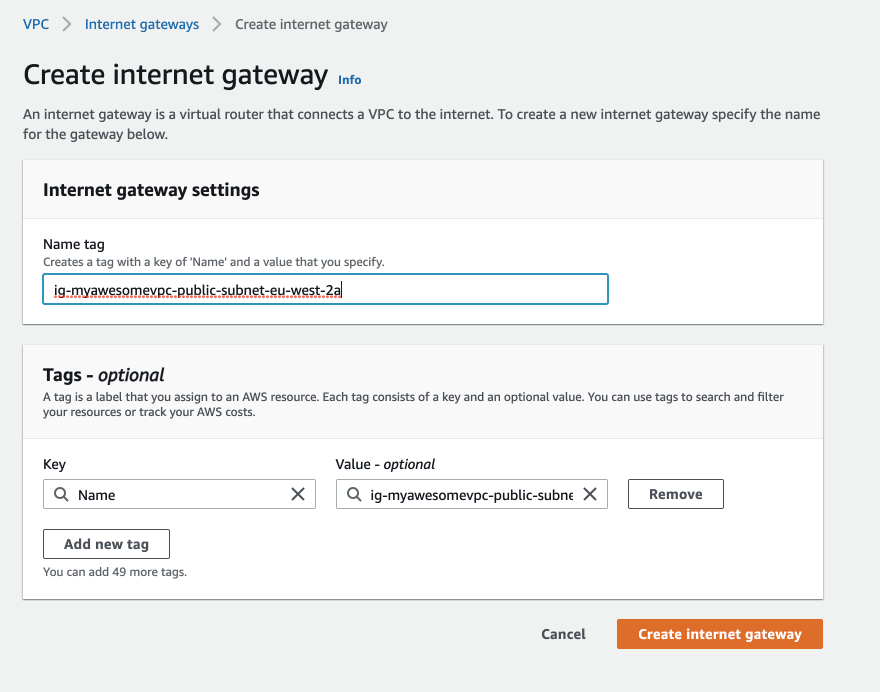
Hit create! Done.
Hit Internet gateways again in the console, then click on the Internet gateway ID in the list.

At the top right, hit actions and then 'attach to VPC' and from there select the VPC we created earlier.

Now when we created our public subnet, AWS kindly created a route table for it, so all we need to do here is associate our new Internet gateway with a new route out to the Internet.
You'll still be under the VPC dashboard, hit subnets, then under subnets, hit route tables and select the link under the route table ID.

This will open up the route table:

Towards the right, hit edit routes

Hit add route and insert 0.0.0.0/0 and then to the right, select the Internet gateway that we created earlier:

Hit save changes.
Okay, cool - now we have a VPC, public subnet, route table and Internet gateway setup. If you want to drop an ec2 instance into the public subnet, all you would need to do is give it an Elastic IP address and you'll be able to access it from the Internet ensuring that you configure the security group for the ec2 instance and lock it down.
This is somewhat easier. As all we are doing is following the steps above but not associating the route table associated with the subnet to an Internet gateway.
You should still be in the VPC dashboard, so again head towards subnets. Again we need to select our existing VPC and we will provide another /24 subnet range.
Fill in the form like this:
- VPC ID, select the VPC we created earlier from the drop down.
- Subnet name, private-subnet-myawesomevpc-eu-west-2a
- Availability Zone, I am again choosing London eu-west-2a as both my public and private subnet are in the same data centre and subnets do not span availablity zones in AWS.
- IPv4 CIDR block, 10.0.1.0/24
- Add some optional tags

That's it!
Now if you drop an ec2 instance into your private subnet, it won't be accessible from the Internet because there is no direct route out to the Internet however, ec2 instances in all subnets can communicate with each other because the VPC has a default router than ensures that all subnets know how to make contact with each other. It is therefore up to you to ensure that routes are locked down and source/destination configuration takes place through ec2 security groups and network access control lists.
There is more to come, I'll write another post that explains how to add a NAT gateway to your private subnet that will allow ec2 instances to access the Internet through a mask but no traffic will be allowed back in directly, therefore it remains private.
You may always want to route the AWS private network into an on premises network through a VPN or MPLS network, again that is for a later post.
20
