20
How to enforce Kubernetes Best Practices with Datree
For June I chose: Datree 🎉 - a CLI tool that prevents Kubernetes misconfigurations from reaching production!
Let’s say that your company has multiple project teams, where developers are deploying their applications to K8s. A DevOps engineer, who is managing the K8s clusters in the company, wants every project team to follow certain rules and write K8s configuration files which follow the best practices.
This way they want to prevent any misconfigurations or security issues from ending up in the cluster when the applications are deployed.
DO:
- Specify a version on every image used in the Pod, instead of the latest tag. Why? Every time that image is pulled, the version will be a different version and might break your code
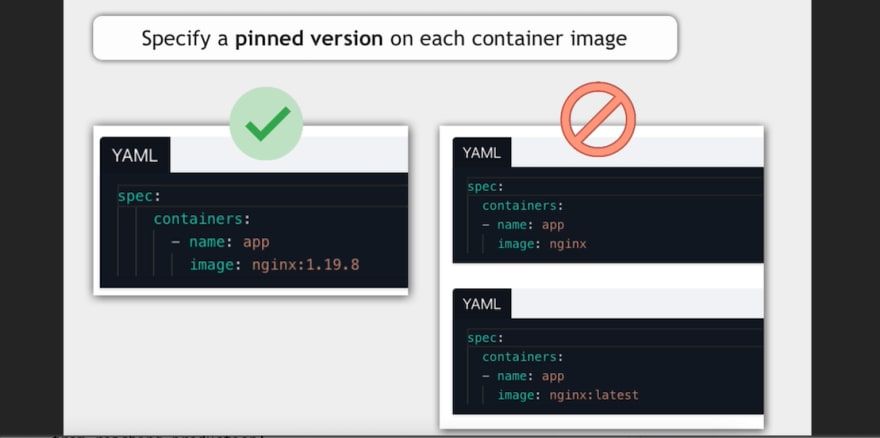
DON'T:
- Run a container with root privilege. Why? Containers are much more secure when their access is limited
- Use deprecated K8s APIs for the components
So to avoid these, the K8s administrators will screen the configuration regularly and check for any misconfigurations or security issues.
After the K8s admins detect the issues in the configuration, they would notify the teams about the issues, which need to be fixed. And this needs to be done for all the clusters across the company. Sometimes the teams may not prioritize the issues or delay the fixes.
But also, if this validation process is not automated, the admins may miss something and the misconfigurations and security issues may actually end up all the way in the production.
So the question is: How can we let developers create those manifests themselves, but at the same time make sure any configuration that ends up in the cluster is correct and follows the best practice rules that admins want? 🤔

It's actually very simple: Datree lets the K8s admins create policies and best practices they want every team to follow, and then run these policies as automated checks as part of the CI/CD pipeline or even earlier in the development workflow as a pre-commit hook, for example.

This moves the misconfiguration checks to the left, preventing them from ending up in the cluster, but also letting developers fix them right away, without the need of back and forth communication from K8s admins, explaining developers why and what needs to be fixed.
It's a command line tool, which you can install with a single command, which means you can install it on any machine and integrate it in any tool and trigger whenever you want, like every time developers commit changes, or create a pull request etc.
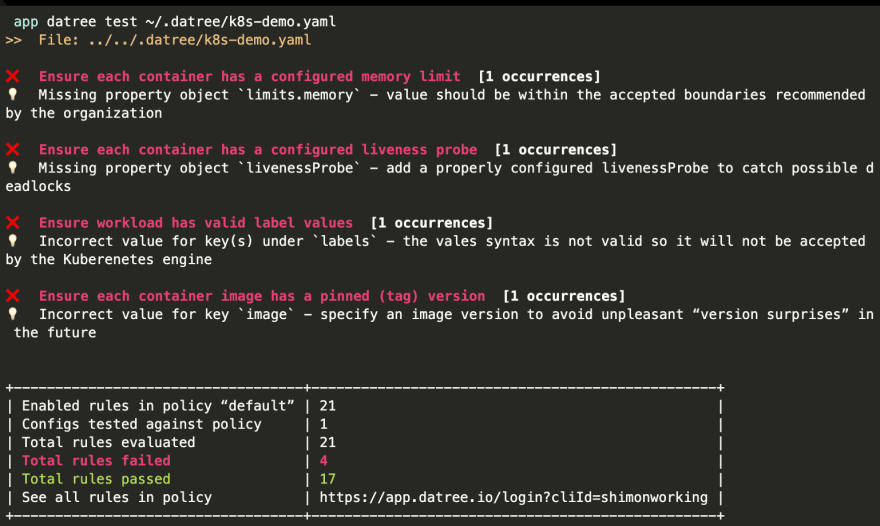
So basically K8s admins, who actually know K8s and how to properly configure k8s components, will create policies with all the rules and best practices once. Integrate it in all the teams' development workflows and in this way make the company-wide consistent policies that all projects will use.
And to integrate it in multiple CI/CD pipelines, you actually don't have to copy and paste the policies and include them in every project. These policies are stored centrally in Datree and not in the project as an additional project file, so by just referencing the policies you can use the same policy in all your CI pipelines.
The following 3 things are validated:
- YAML: Is the file a valid YAML file
- Kubernetes Schema: Is the file a valid Kubernetes file
- Policy: Is the file following your Kubernetes policy
Also in addition to you being able to create policies, Datree already gives you a list of built-in policies, which already covers almost all the best practices. This means, once you set it up, you can already start validating your YAML files with these built-in policies. 👍
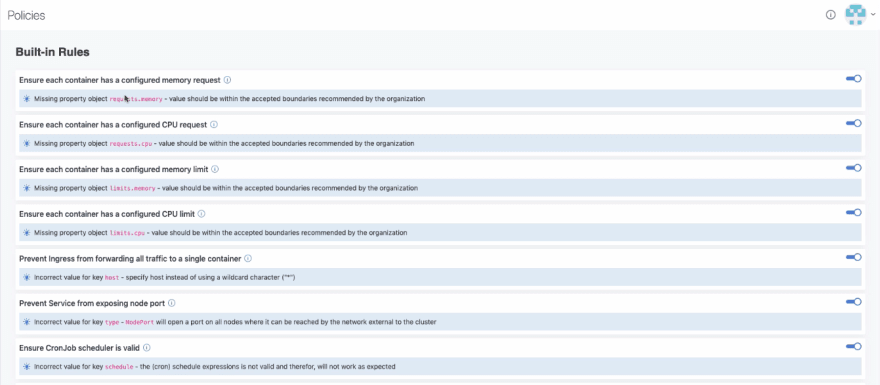
In the video, I will show you how to easily set up Datree and start validating your K8s configuration files right away:
More awesome tools coming up next on this series, so stay tuned for it! 🎬 😊
Like, share and follow me 😍 for more content:
20
