47
Writeup: HackTheBox Mirai- Without Metasploit (OSCP Prep)
Hello Again All!
Here with another write up and this time it will be Mirai from HackTheBox.
Difficulty level: Easy
So lets begin!
Nmap -sC -sV -T4 -oN nmap.txt 10.10.10.48
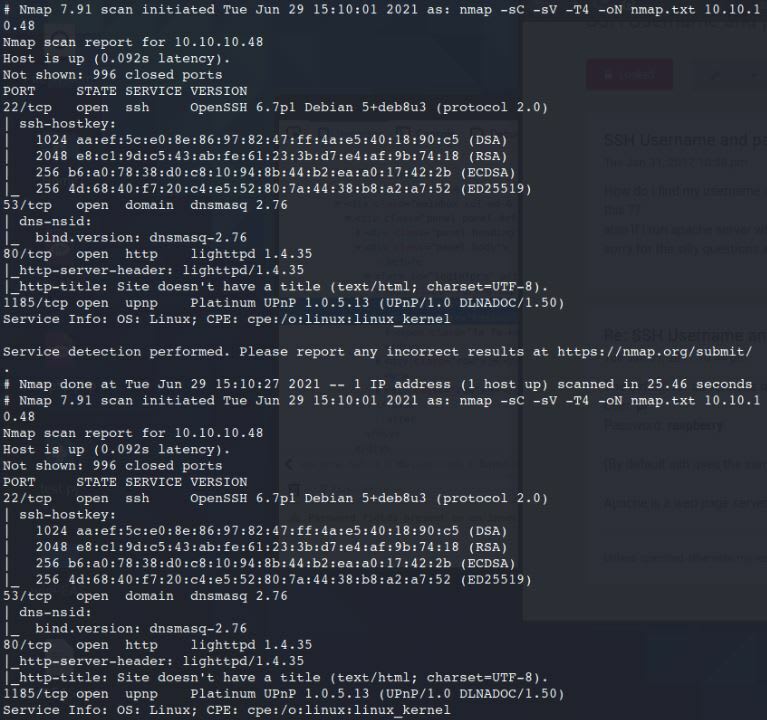
Open Ports displayed:
Let's head over to the website to see what is there.
Nothing appears to display when going to the site so let's try the following.
Right-click on the page.
Still nothing is displaying.
Alright, lets check out the other ports open on the box.
ssh 10.10.10.48

So no luck with trying to just SSH into the machine. I am going to run a nmap Vuln Scan on the machine to check.
Nmap --script vuln -oN vuln.txt 10.10.10.48
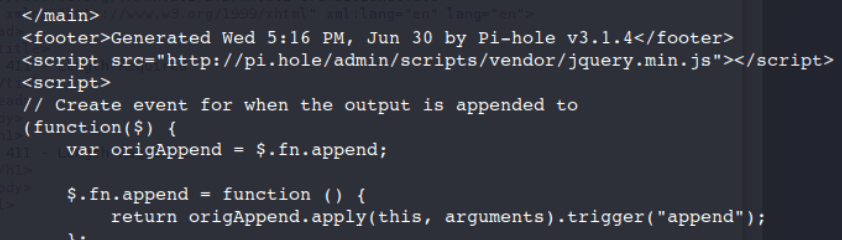
If you scroll down to the middle of the page there is a reference to something called "Pi-Hole".
I am going to try something else to see if anything comes up.
curl -vvv 10.10.10.48
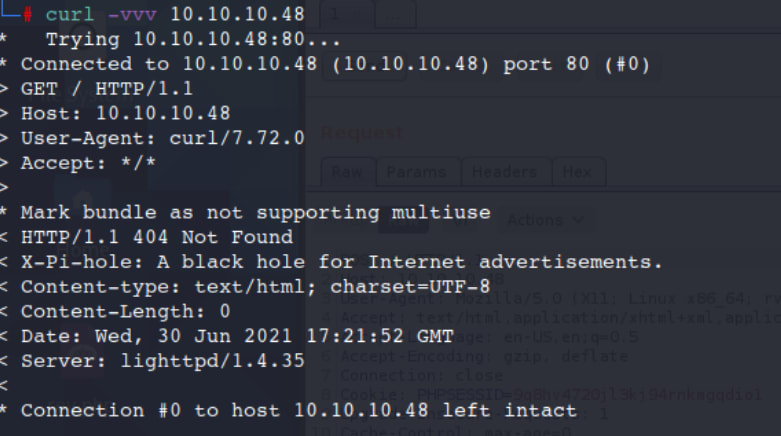
So we can now see again there is something with "Pi-Hole" going on here.
Directory Busting is usually helpful when trying to find hidden directories on a site.
dirb http://10.10.10.48
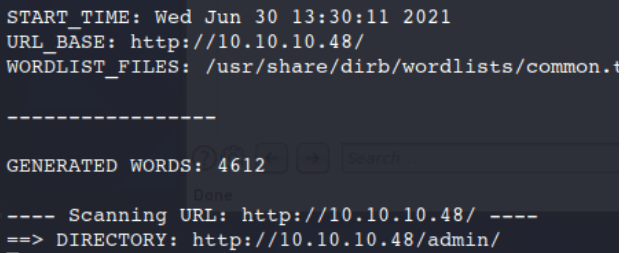
After a few minuets of this running we come back with a success with /admin/.
Great, lets now head over to the site to see if there is anything there.
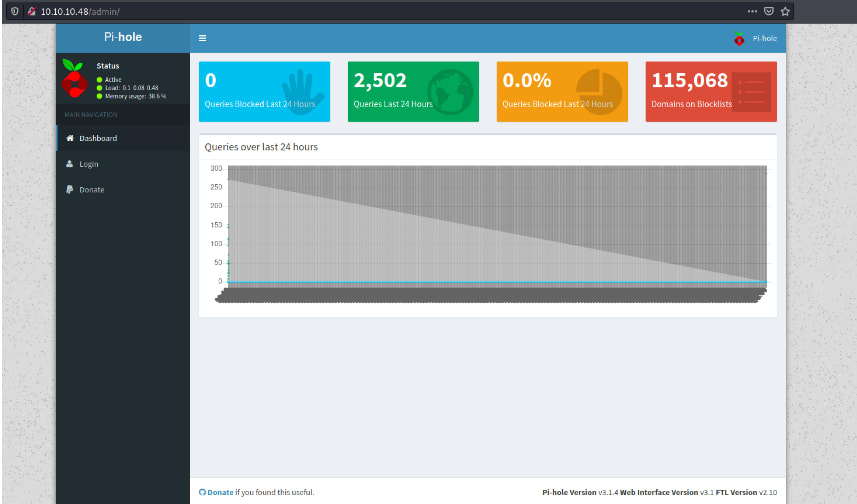
So if you never heard of Pi-Hole or Pihole this is a linux network-level advertisement and internet tracker blocking application which acts as a DNS Sinkhole and/or DHCP Server.
After playing around withthe site for a few minuets I head over to the Login landing page.
So I tried doing a few things here, attempted to use Hydra to gain access on the site as well as use hydra for the SSH login but no luck. From here I head over to Google.
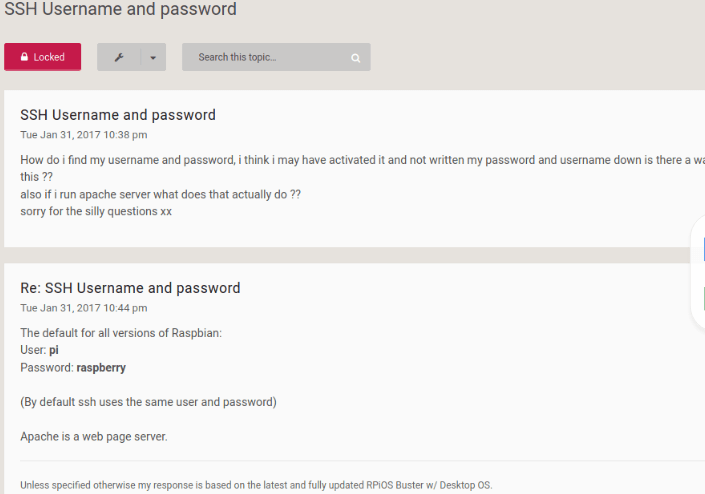
So it looks like the Username/Password gets set to pi:raspberry.
I tried using this on the login page but that didn't work so I turned to the SSH login.
ssh pi@10.10.10.48
raspberry
raspberry
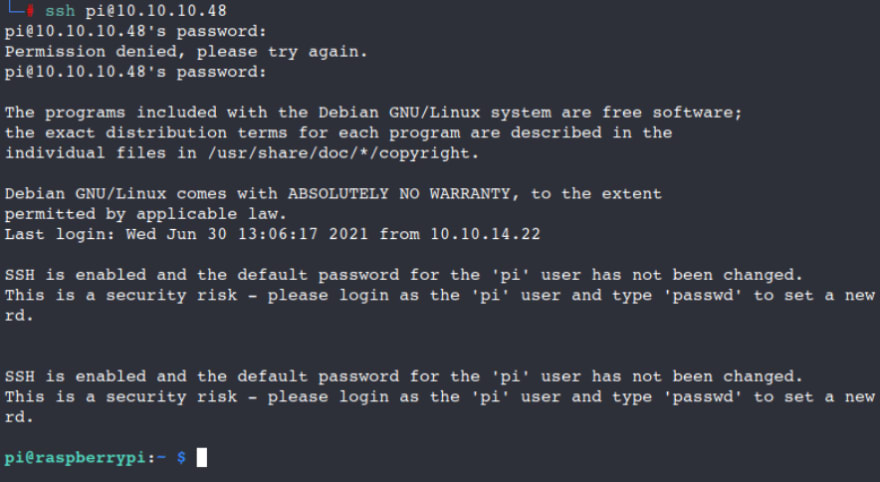
Looks like we got our first access to the SSH server!
wc user.txt
Lets run some Sudo commands.
sudo -l will list the allowed and forbidden commands for the invoking user on the current host.
sudo -l

Welp that is interesting....
Alright I am going to try and switch users.
sudo su-
whoami
whoami
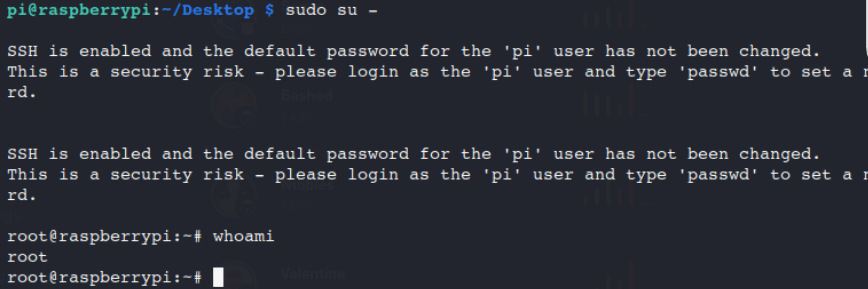
ls
cat root.txt
cat root.txt

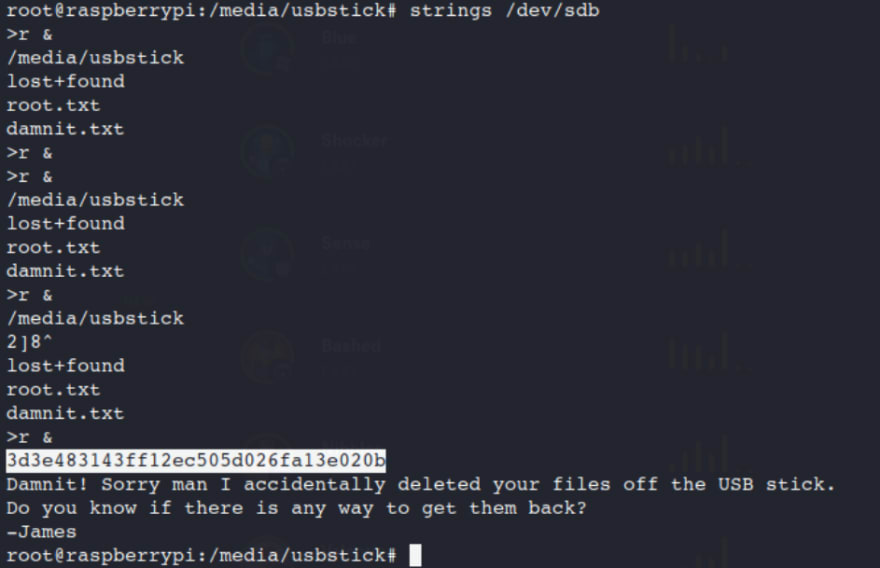
Looks like someone removed the root.txt from this file and its in a USB stick....
Take the time and go into the files and see if there is anything that pops-out at you.
ls -la
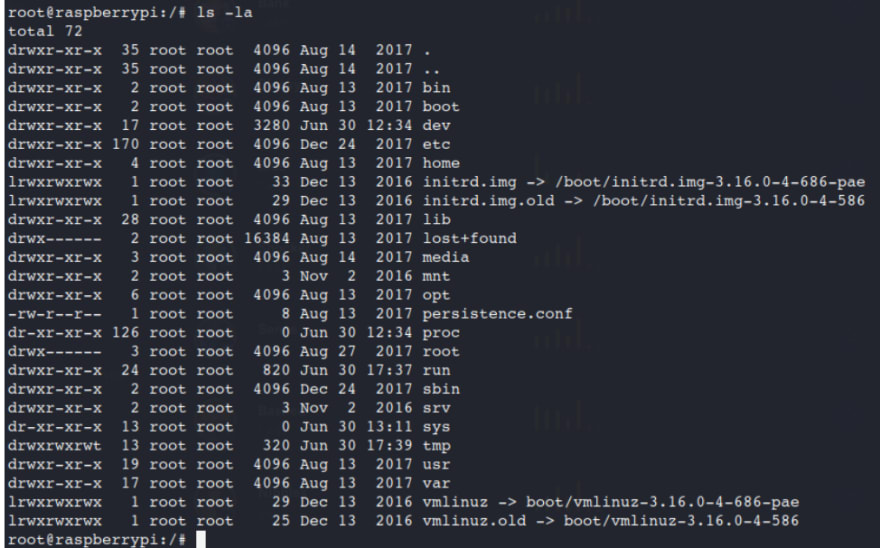
After some searching I come across the /media location with a usbstick there.
cd media
ls
cd usbstick
cat damnit.txt
ls
cd usbstick
cat damnit.txt

It appears that someone else deleted your files off the usb stick.
df -lh
Will show free disk space and lets focus on the /media/usbstick

You can use Strings to look for characters or you could have used cat as well.
strings /dev/sdb
Thanks for stopping by!
47
