26
Getting Started with AWS Config, CloudTrail, CloudWatch, S3, SNS
Security is one of the major concerns in any environment, whether you are planning to run a start-up or having an enterprise, you should always consider security before anything and have a zero-trust model.
It is better to be proactive and secure your resource than being a reactive and start implementing security after an incident, some of the reasons are:
- Save money.
- Save efforts.
- Availability of your services.
- Business reputation.
- And many more.
What is AWS Config?
AWS Config is a service that enables you to assess, audit, and evaluate the configurations of your AWS resources. Config continuously monitors and records your AWS resource configurations and allows you to automate the evaluation of recorded configurations against desired configurations. With Config, you can review changes in configurations and relationships between AWS resources, dive into detailed resource configuration histories, and determine your overall compliance against the configurations specified in your internal guidelines. This enables you to simplify compliance auditing, security analysis, change management, and operational troubleshooting.
Source: AWS Config
In this demo, we will set up AWS Config, assign a rule to it, set up AWS CloudTrail, enable CloudWatch to monitor CloudTrail, set up S3 bucket to store our log files, and set up Simple Notification Service to receive notifications through email.
With all that being said, let’s open the console and start setting up AWS Config:
Login to your AWS account
Click on all services, then you will find Config under Management & Governance Section, click it:
It will take you to AWS Config’s dashboard.
Click Get started.
Now you can start setting up your Config,
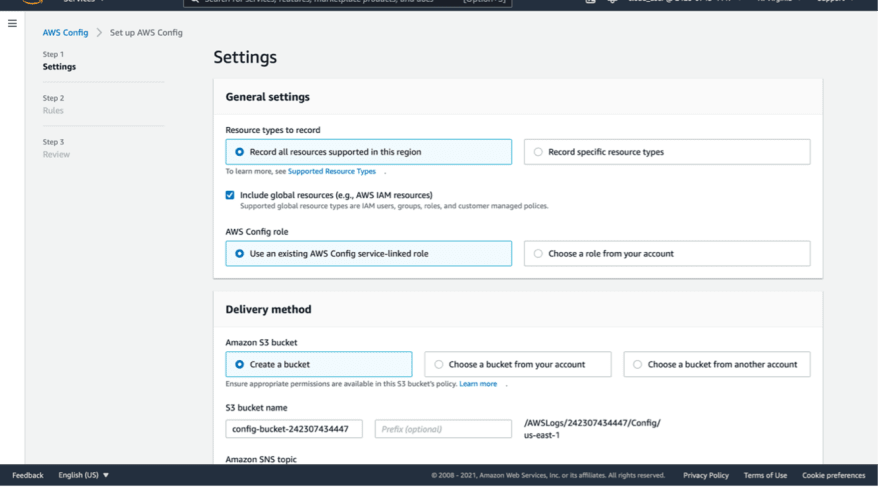
For the resource type; you can choose Record all resources in this region, this will allow config to record all your resources in the region you’re currently using, and you can check the box below which says “include global resources” this will also get the resources that operates in a global basis such as IAM.
Now you will need an S3 bucket to store your config log files,
you have the option to choose an existing one or create a new one directly from Config’s settings, and it will suggest a name for your S3 bucket as you can see in the screenshot below.
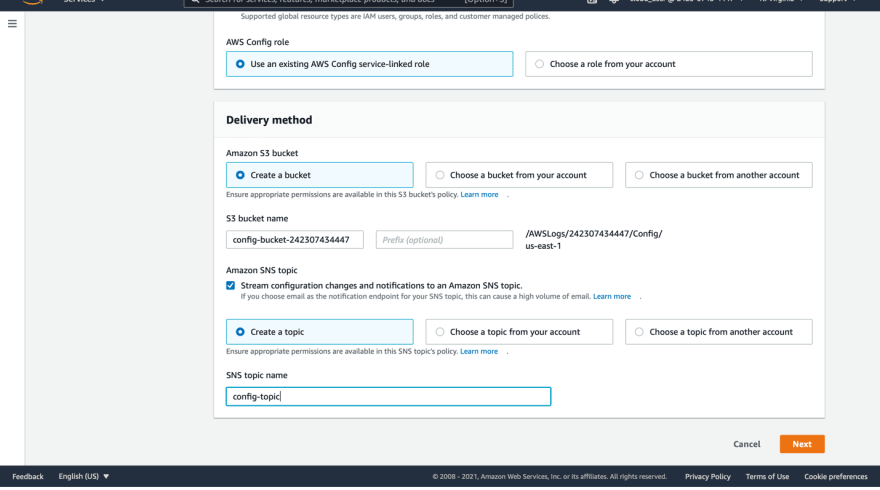
By checking the box for SNS topic you will set up a Simple Notification Service (SNS) topic to provide you with notifications related to your Config.
You have the option to create a new SNS topic or choose an existing one whether it’s from your account or another account.
For this demo, I will create a new SNS topic and give the topic a name: config-topic.
Then you can click next.
It will take you to step 2: to assign rules.
As you can see below there are more than 150 rules ready to use, provided and managed by AWS,
but of course, you have the option to create your own rules.
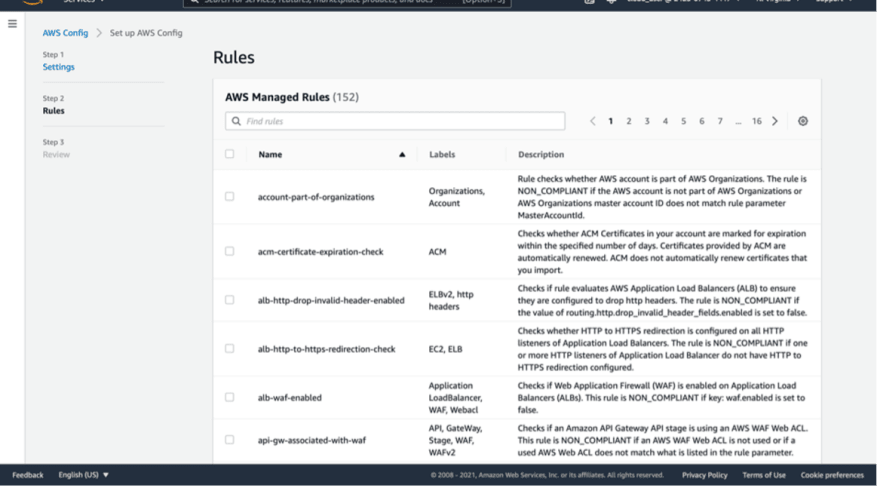
For this demo, I will choose an AWS managed rule.
Cloudtrail-enabled: this rule will periodically check whether AWS cloudtrail is enabled in your account or not.

Then click next and review your configurations then click confirm.
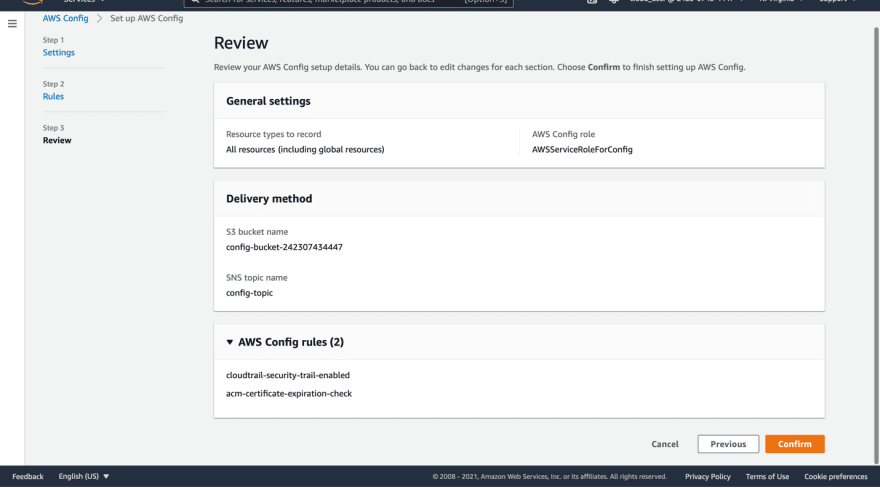
Your AWS Config Dashboard will open, this is where you can add/edit/delete rules, check compliances and basically manage everything.

Now let’s set up a CloudTrail, you can find it under Management and Governance.
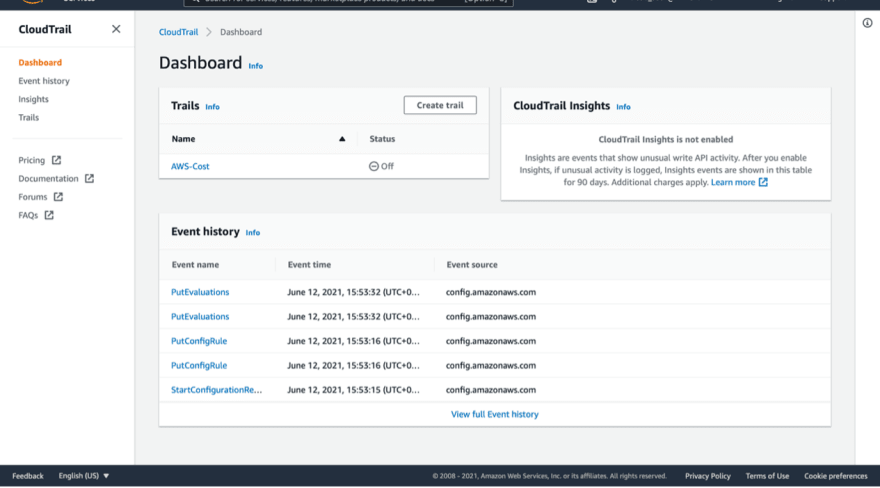
Once you’re in the dashboard, click create trail.
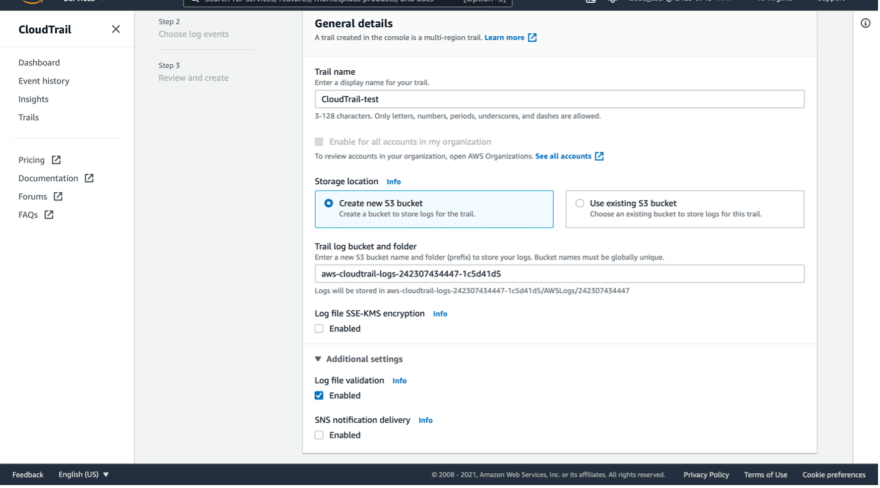
Give it a name and select where do you want to store the logs;
You can use one of your existing S3 buckets, or create a new one directly from here,
I will create a new one and it will automatically provide a name for it (you can change it) you also have the option to encrypt log files using KMS, for this demo I will keep it as it is.
You can also enable Simple Notification Service (SNS) and associate it with this Trail.
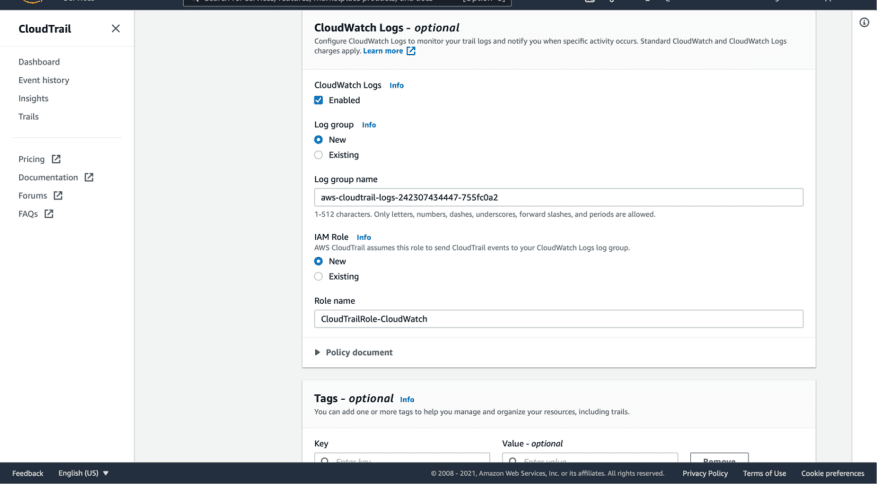
And you have the option to enable CloudWatch logs; which will monitor your CloudTrail logs.
I will enable it and choose a new log group then give it a name (It will provide it automatically, but you can change it).
Then you will need to assign an IAM Role to enable communication between CloudTrail and CloudWatch, I will choose a new role and give it a name.
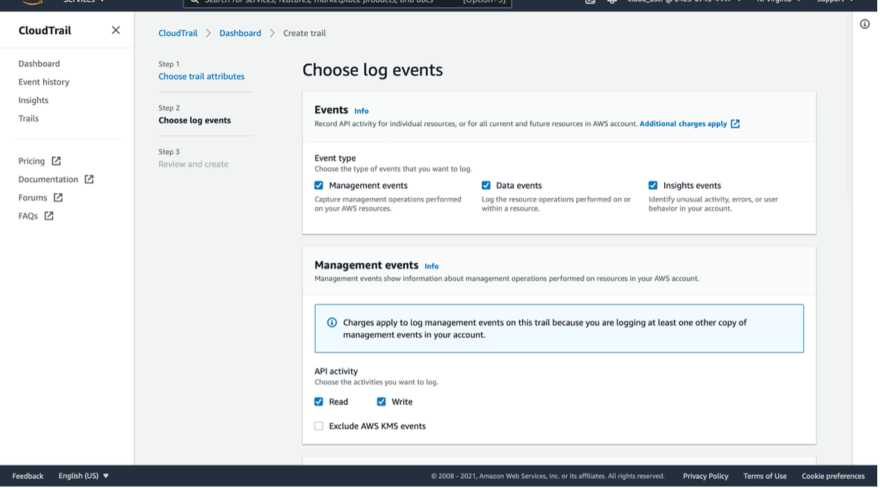
You will select the type of events that you want CloudTrail to log, I will select them all.
It will ask you to specify the kind of API activities to log for the management events, I will choose the read and write activates.
For the data events, it will ask you to select the source of data, I will keep it S3; you can select a specific S3 bucket, or all current and future S3 buckets, I will keep it for all S3 buckets.
In insights events, you can enable the API Call rate to measure any unusual activities.
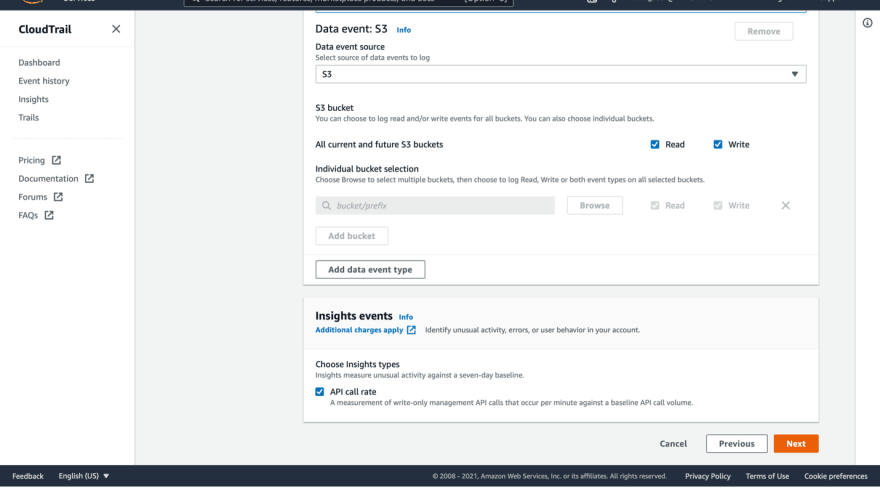
Click next, review your settings, and click create trail.
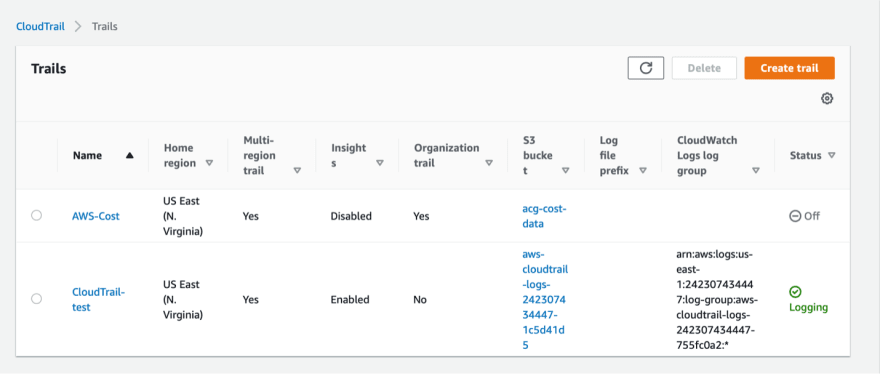
Now you can see our trail “CloudTrail-test” is enabled and the status is Logging.
Let’s go to S3, you can find it under Storage.
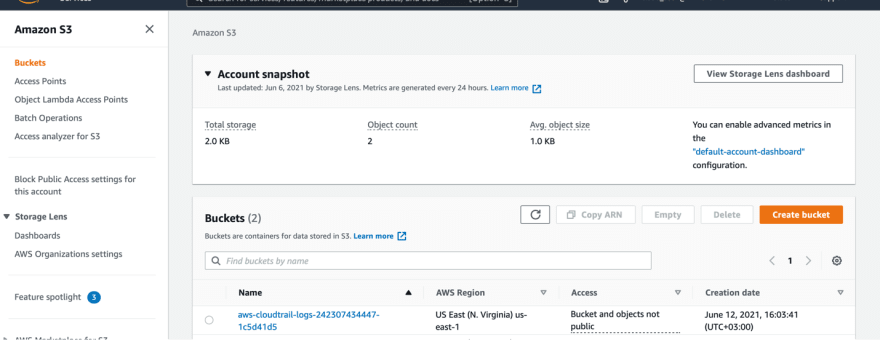
You can see our S3 bucket has been created, and we can find all CloudTrail logs inside it
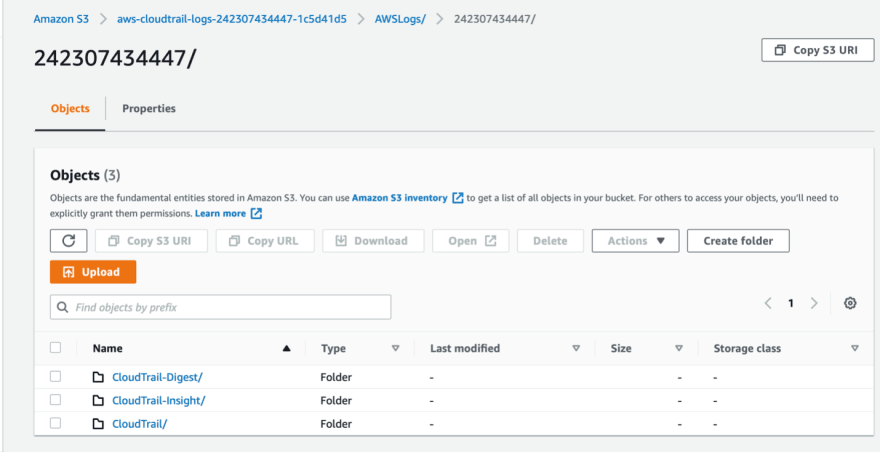
When you click on it you will find our folders that contains logs from CloudTrail.
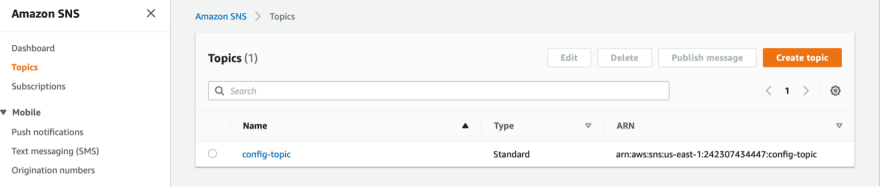
Now let’s go to Simple Notification Service (SNS), you can find it under Application Integration.
You will find the Topic that we created earlier (while setting up Config) here -you will need the ARN in the next step-.
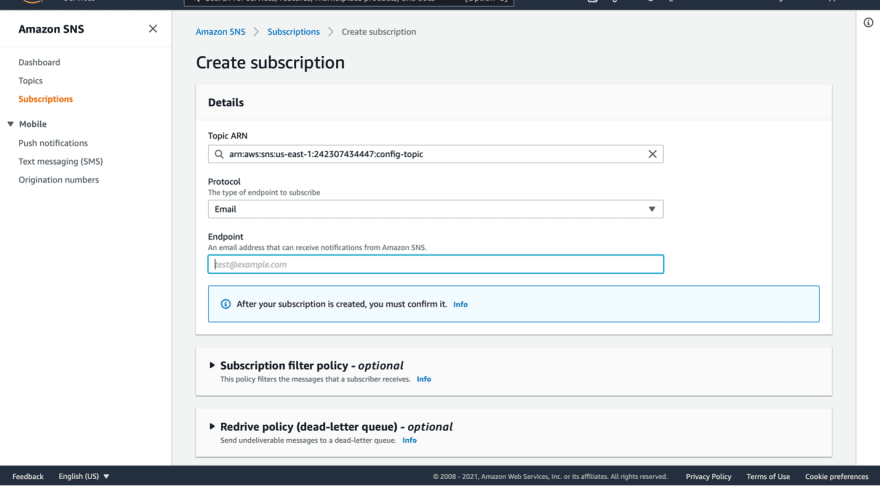
Let’s connect it to our email to receive notifications there.
Click on subscriptions (you can find it on your left-hand side of the screen) click create subscription and fill the necessary details.
Select the Topic that you want to connect to your email (your topic's ARN), and in the protocol section, select email.
For the endpoint, add your email address then create the subscription.
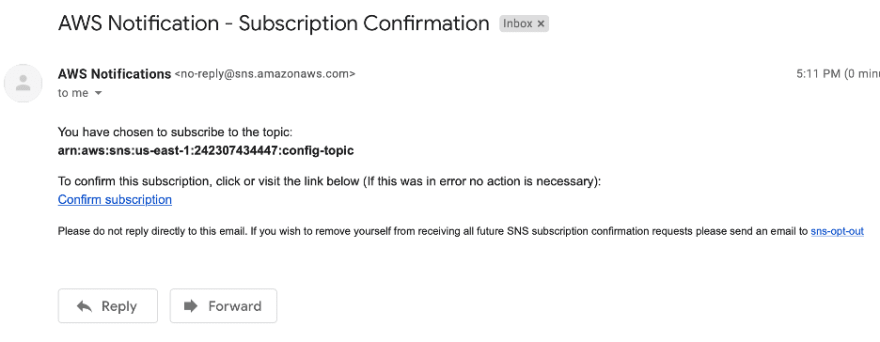
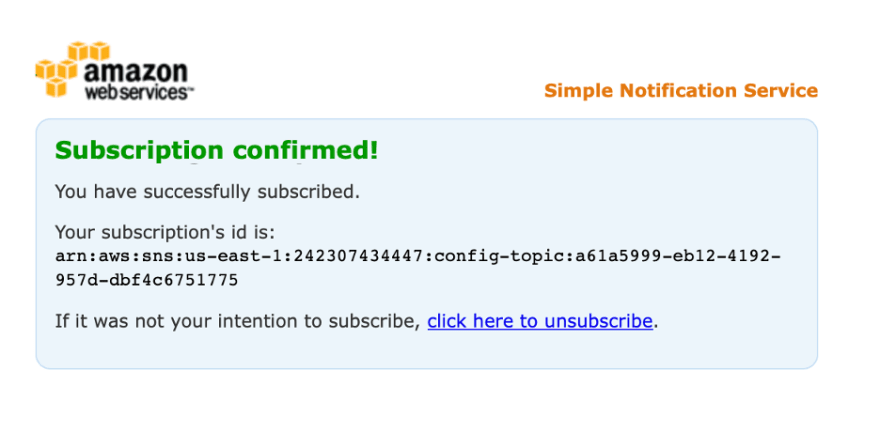
You will receive an email to confirm the subscription, click on the link that says “Confirm Subscription”.
It will open a new web page that confirms your subscription, with your subscription ID and an option to remove the subscription.
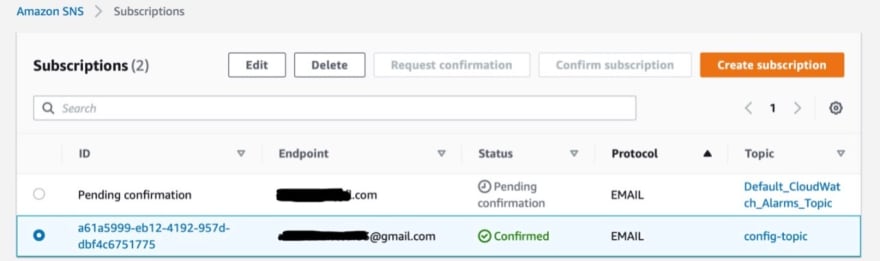
If you go back to SNS Subscriptions, you will find your subscription ID, your email address and the status is confirmed.
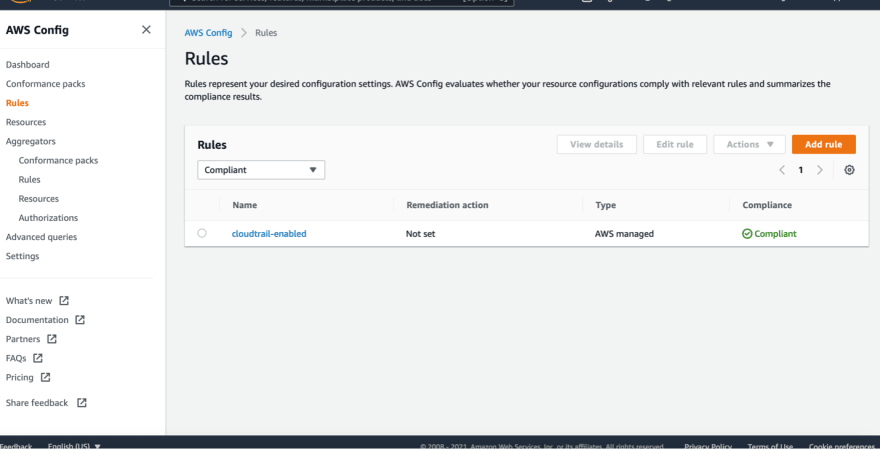
If you go back to AWS Config, you will find your cloudtrail-enabled rule compliant now.
We now have a centralized configuration dashboard associated with chosen rules to evaluate our security, CloudTrail to audit API calls, S3 bucket to store all log files and receive notifications via email.
26
