23
AWS VPC, how to add more IP addresses?
Sometimes we need to add new CIDR range, or increase number of available IP addresses in our VPC. Reasons for that may be different. Logical separation may be one of them, another can be simply caused by our bad design.
If you are working with AWS VPC, and you face this kind of problem, no worries, AWS is giving very simple option to make you happy.
Some time ago it was impossible to add new CIDR to the VPC. We had different ways to solve the problem, like create new VPC and move everything there, or just peer two VPCs together. Today you can add new CIDR to existing VPC in a few clicks (or commands). I show you how to do it in very short exercise.
So, let’s get started.
Two schemas below show the state of the VPC we have now, and what we want to achieve. The issue is simple, we have two subnets, and no free space in VPC to create another. But we need to do it.
You have the VPC with CIDR 10.0.0.0/23 it gives 512 IP addresses (from 10.0.0.0 to 10.0.1.256). You also have two subnets, both with /24 range. Each subnet contains 256 addresses (in fact, 251 is available, as AWS reserves 5 of them for their internal needs). As you can see, there is nothing left in our VPC.

And now, you realized you need more IPs. No matter why - you need logical separation for layers, you need more resources, it doesn’t matter. In this case, you need to add more CIDR ranges to your VPC. Below is the expected state. In this example we want to have two more subnets with the same number of IP addresses available.

Fortunately, this task is very easy.
What you need to do is go to the VPC service, select the proper VPC, click actions and ‘Edit CIDRs’.
Here you are able to modify CIDRs for theVPC. You want to add new IPv4 range, so you need to find proper section.
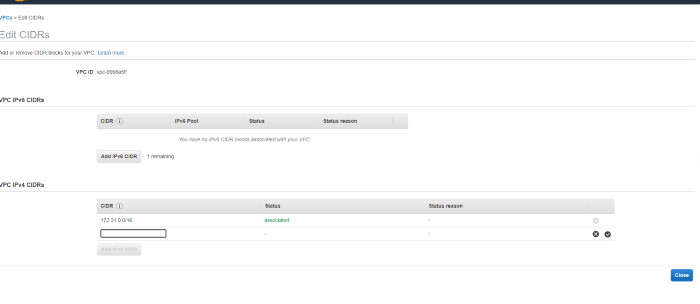
and add the new CIDR range. In this example I used 10.100.0.0/23.
As you probably know, AWS is taking care about traffic inside the VPC. So, when you are creating the VPC, AWS is creating routing tables for you. In case of using default route table, all needed changes will be provided automatically. If you have custom route tables — you need to check them and fix if needed.
Let’s check the default route table.

As you can see, the default routing was modified with new CIDR.
Now it is time to add new subnets using the new range. You need to do it in exactly the same as always, this time you set the CIDR for those subnets with 10.100.0.0/24 and 10.100.1.0/24 ranges. This gives another 512 IP addresses.
Of course, new subnets must be associated with route table (in this exercise I use default RT, but in “real world”, I do not recommend it).
Now it is time to go to the VPC and check the subnets.
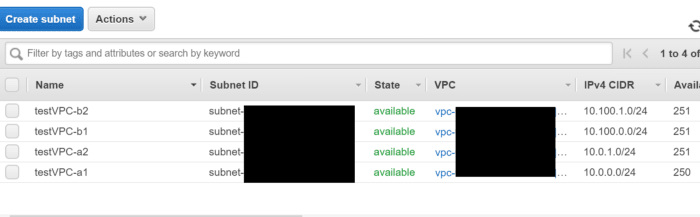
You can find the IPv4 CIDR ranges very easily.
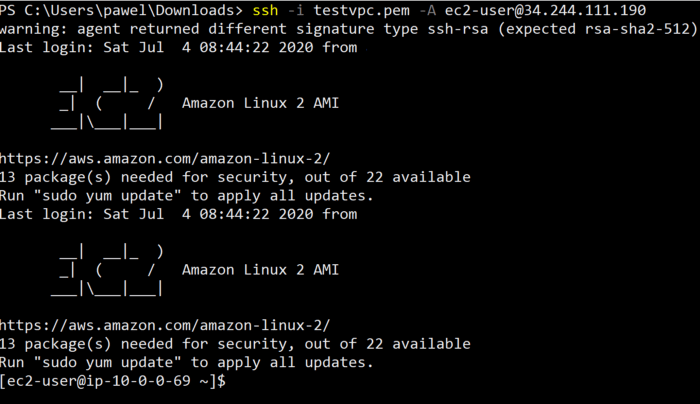
It is time to run the test. How I checked it for you? I’ve created two ec2 instances, on in “a1” second in “b2” subnets. And simply ssh from one to another. Obviously, the Security Groups were set accordingly.
You can check the IPs of ec2 instances on screens below by checking their hostnames.
Extending the CIDR ranges in AWS VPC is very easy. It can be done in minutes. But remember, this approach doesn’t extend your defined CIDR range. It simply add another range to your VPC.
What if you want to extend existing range?
if the CIDR is not primary one (so defined when you created VPC), you need to disassociate CIDR from VPC, and simply associate bigger one.
if the CIDR is primary one… well, you cannot extend.
As you can see, you cannot “just” extend the CIDR range. Logically, it means adding a new range.
Also, there is a limit for CIDR ranges associated with VPC. You can have 5 CIDR ranges for IPv4 (primary and four of secondary CIDR ranges) and only one for IPv6. For IPv4 you can request increase to max 50 ranges, but you cannot do that for IPv6.
23
