86
🙌 How to get rid of vulnerabilities with just NPM 👀
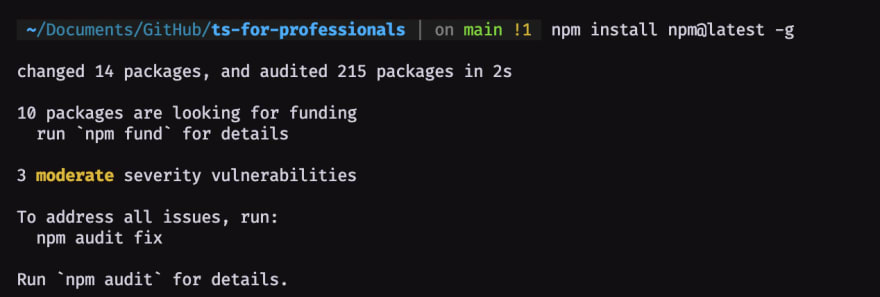
Sometimes when you're trying to install or re-use some kind of global package on the NPM environment, you will get messages telling you something like this:
As NPM itself will suggest, you, should audit them, to kindly fix them ☺️

But let me make it clear,: That is for sure, not the real way to "Security" audit things, but it is for sure, the minimum safe way that you must stay (at least) for the greater good!
This kind of vulnerability could became a real problem, especially when your packages are global packages.
I mean, When you're using the "-g" flag to make it system wide available.
For this, its a minimum good practice to also use things like NPX. But... if you're that lazy, as I am, here is this small shenanigan that could help you to keep yourself a bit more safe. 👀
On the bash, or terminal, type:
$ npm install npm@latest -g
The $ means that you're into the bash or at least on a terminal like prompt 😅
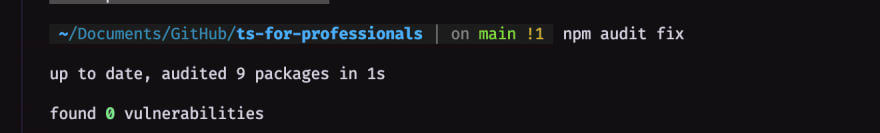

Yes, that is totally accurate! 👌
NPM audit will check inside the package you're on (or even none if your not). It will not check the for entire "NPM" global environment.
OMG - David504
Context for the quote: https://www.youtube.com/watch?v=B6LpzJLrhpw
The right way? use rust 🦀 . Joking, you could use NPX, but if you don't want to (as I don't)... wait there!
You know what NPM people loves? Packages. 📦
And so we does! We love packages 🥰! But what about installing another global package to fix global packages?
Now you must say: That looks sooo great!
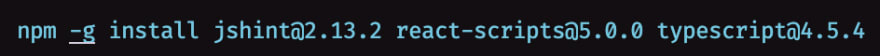
Then, Kindly type into the terminal this, while praying to NPM's gods:
$ npm install -g npm-check-updates
The output gonna be like:
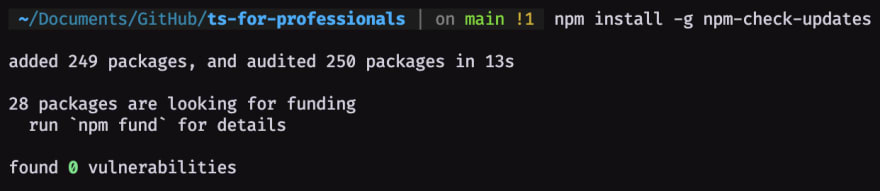
Thanks god that wasn't any vulnerability inside the vulnerability checking package 😮💨
If all went good till now, guess what? You will have another package globally available to use! 😌
(っ◔◡◔)っ ♥ legacy code vulnerabilities ♥

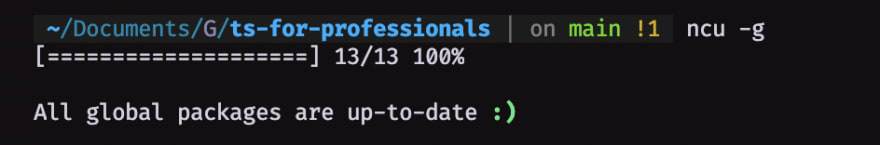
But, how do we use it?. Again, from the terminal, type:
$ ncu -g
Output should like:
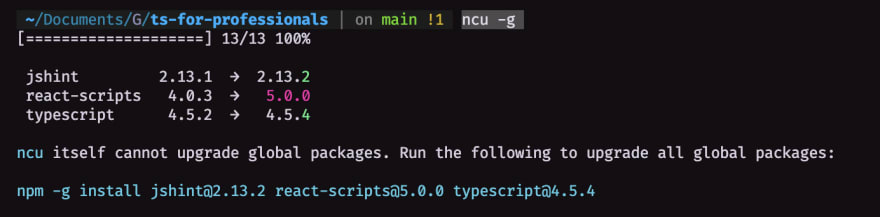
On the last line, it will give yourself the minimum needed updates to fix common vulnerabilities that were fixed on newer versions! 🤩
Now... lets just, as always: CTRL+C -> CTRL+V stuff. 😎

Yes, that is again, fairly right 🤦♂️
What you will need to execute, instead of the other command that I told you to run is this one:
curl --proto '=https' --tlsv1.2 -sSf https://sh.rustup.rs | sh
and you will have Rust and Rust's Cargo!
You got rid of the Global Packages vulnerabilities (from themselves) by upgrading them. But those packages (sometimes) depends on other packages...
I told you that NPM's guys really like packages ¯_(ツ)_/¯
There will be, always, some vulnerabilities left inside these (dependencies). But not within being into a Global Package itself, then we're kinda good to go.
And to make sure there is not left, you can re-check it by doing so:
$ ncu -g
(to check if there is the need to upgrade any to a safer version)
If you gonna stand with just NPM without NPX please, at least do this.
I will soon write a how to NPX... or not
Thanks! Follow me on the Dev Bubble on Twitter
86