152
How to copy a software protection dongle
The most efficient method of sharing a USB dongle over the Internet or a local network is with the dedicated functionality of the dongle copying software solution Donglify.
Donglify is a sophisticated software application that enables users to create a virtual copy of a USB license dongle so it can be accessed remotely over a network. All network connections are encrypted so data transmission is fully secured. The app even lets you share a single physical USB dongle simultaneously with multiple remote users.
The instructions provided below describe the three different ways of using protected software on a network by copying USB dongle keys. The software runs on the Windows platform and can be used in the following ways.
These steps enable a user to remotely connect to a computer with a physical connection to the required security key. Sharing the device across the network lets you use a virtual copy of a USB dongle to run the protected software resource from any remote location.
- Start Donglify on the two machines and log into the software using identical credentials.

- Click "+" on the server to open a window from which you can view the USB dongles that are available to be shared. Select the device you wish to use and click “Share”. USB copy protection dongles that display a “Multi-connect” icon can be shared simultaneously with multiple users.

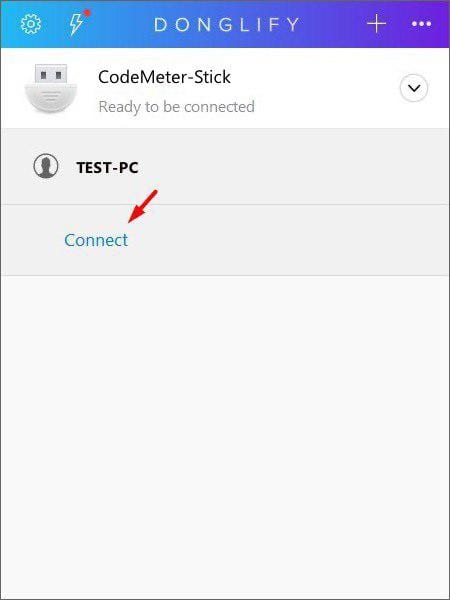
- Open Donglify on a client computer and locate the dongle shared by the server. After clicking “Connect”, the dongle key copy will be recognized by your system and give you the same level of functionality as if you were physically connected to the device.
Click “Disconnect” when you are finished using the dongle and the connection will be terminated.
Creating a token provides a secure digital key that can be shared with other users. Sharing a token with a colleague lets them use Donglify’s functionality without accessing your Donglify account. This keeps your personal information safe and gives you control over who can access a specific copy of a dongle key. If you delete a token, the individual using it is immediately logged out of the Donglify account.
Create a token using the following simple steps.
Log into your online Donglify account.
Open the “Tokens” tab and click on “Create Token”.
Choose a name for the token and click “Create”. It will immediately be listed and available to be shared.
Copy the token and share it with any users using a text message, email, or any other method.
If you need to delete the token, click the red “X” next to its creation date.
To use Donglify using a token, use these steps;
Download and install Donglify on the computer that will access the dongle remotely.
Start the application, provide the token, and log into the account.
Note: Token can be used simultaneously on multiple machines.
You can invite users to remotely access a security key. This enables you to keep your account details private while letting others access a security key remotely. Follow these steps to send an invitation to use a security key:
Physically attach the dongle to your computer. Launch Donglify and click “+” to view the devices that can be shared. Locate the key you want to share, check its radio button, and click “Share”.
Send an invitation directly to another user by typing the email address associated with another valid Donglify account and clicking the “+” icon. Donglify displays the email address and you will receive a “Connected” message when your invitation has been accepted.
When you want to end the remote session, click “More” next to the user’s email address and choose “Disconnect”.
Donglify is useful in a wide variety of situations and to a range of IT professionals.
Licensed software developers can distribute a product trial to many customers without sending them hardware dongles. This saves time and money and lets the developer control when the dongle is removed from the Internet, shutting down access to the software.
Large or medium business owners who have remote technical staffs and employees can benefit from maintaining their hardware dongles in a centralized location and sharing them remotely as they are needed.
Service providers who need to perform software maintenance for their customers can benefit from the remote access to security keys provided by Donglify and can provide clients with more customized service.
Owners of licensed software products protected with a USB security key benefit by having the ability to use their licensed software without needing to carry around an extra piece of hardware.
As you can see, copying a dongle can be important in a variety of situations. It greatly expands the utility of protected software by eliminating the need to have the security key physically present when using an application. With the help of Donglify, using protected software requiring security keys remotely becomes a simple process.
152
